[FIRMWARE] Itus Networks Shield Firmware Upgrade *WIP*
1 ...
6789101112
1 ...
6789101112
|
Administrator
|
I'm not sure what Itus had in mind, since I don't see a need for even the Bridge mode. I can't see picking the transparent bridge over the router configuration but my use cases are pretty straight forward.
I've gotten success in starting to setup the individual modes. Right now, I want to set it up so that everything is self-contained in a single image and sets itself up based on the slot it is put into. It beats having to try and keep up across three repos. Once I get it shaken out, I'll put up a router image for those who want to test. I'll also be sending out an email to the forums registered users asking for test subjects :D.
Running Itus Shield v2 Firmware
|
|
Sign me up please :)
Running v2 Firmware
|
|
Administrator
|
Turrican, I sent you an invite through Google Hangouts.
Running Itus Shield v2 Firmware
|
|
Administrator
|
Gnomad,
I finally got Snort 3 to compile and install, but the current /etc/snort/rules/snort.rules error badly. Any idea if there are changes between the 2.x and 3 rule defines?
Running Itus Shield v2 Firmware
|
|
Yeah, looks like the syntax has changed. There's separate v2 and v3 downloads available here https://www.snort.org/downloads/#rule-downloads for "community-rules". But if we want to include the additional emerging threats I can only find reference to v2.9 https://rules.emergingthreats.net/open/ (snort-edge is also 2.9 based) We can keep an eye out for changes, but I'd say v2.9 is working well enough for now. Sorry for my radio silence too - super-busy period with work.. On Fri, 1 Nov 2019 at 14:14, Grommish [via Itus Networks Owners Forum] <[hidden email]> wrote: Gnomad,
OpenWrt SNAPSHOT, r10391-3d8d528939
|
|
Administrator
|
Well, see, thing is... Snort 2 kinda stopped working. They changed something that'll require me building snort without appid. One of the appid modules calls library calls that aren't available under musl (the toolchain), just x86. So on one hand, 2.9.x can be made to work (probably) but without appid. Or, go to 3 beta and get started early on the stuff. It has appid working. If we can decide this, I can put the call for testing out and we can see if anyone answers. Maybe someone good at snort configs will show up. 3 should also offer a greater ability to set rules. Dunno. Comments? On Fri, Nov 1, 2019, 3:44 AM Gnomad [via Itus Networks Owners Forum] <[hidden email]> wrote:
Running Itus Shield v2 Firmware
|
|
What's appid? Benefits? If we went to snort 3, I expect we'd be resigning ourselves to base community-rules for a while - I haven't seen any roadmap for emerging-threats to move to it anytime soon, and even if you can find snort-fluent Shield users I can't imagine any would have the bandwidth to maintain a 3.x equivalent set.. On Fri, 1 Nov 2019 at 15:55, Grommish [via Itus Networks Owners Forum] <[hidden email]> wrote:
OpenWrt SNAPSHOT, r10391-3d8d528939
|
|
Administrator
|
Just a quick update - I'm still alive! Yay!
Actually, I spent some time in hospital for what seems no reason. I'm hoping to pick this back up shortly. AppID identifies the filetype (using Magic File) of inbound files, regardless of their extension. So you could block file types with mismatched extensions. Also should allow a whitelisting of specific file types so the Shield won't scan them. I'm going to have to dive back into the repos and see what's new, as well.
Running Itus Shield v2 Firmware
|
|
Administrator
|
Hey All!
So, I've done some updating, and of course it broke some things.. Every time the kernel updates, I have to repatch the source for the Marvell Octeon III PHY network drivers, and that's a pain sometimes. But.. I've got it updated, I've got snort3 installing instead of 2.x. I bit the bullet and did a source compile on my local machine for Snort3 so I could get to the snort2lua program. Snort3 uses LUA based rule and configuration files, so I have to build all of this out and moved over. Snort3, I think, is still kind of "new" when it comes to OpenWrt since it doesn't seem to move anything over in the compile that is actually needed (like the default .lua files, for example) Also there now seems to be support for WireGuard. This could be useful for those who want to monitor everything going thru the Shield in real time. I am still building and testing, but for anyone who wants to test, I'll put up a version shortly assuming it doesn't break anything.
Running Itus Shield v2 Firmware
|
|
Administrator
|
I'm going to put the driver patch file I put together (was based on 7 separate patch files) for the Octeon III network interface. This was probably the single biggest issue I had getting anything to work. It would compile fine, boot, etc, but the network showed 8 interfaces and nothing worked :D
The patch file might serve anyone else looking to make something with the Shield in some way, hopefully making it easier on them. In theory, the box can run anything that has a mips64 version (I was looking into pfsense until I realized they don't, for example). When whoever it is doesn't support the Shield, you can roll your own as everything else is bog-standard except the network. 700-Cavium_Octeon_iii_network_driver.patch
Running Itus Shield v2 Firmware
|
|
Administrator
|
First, in case you hadn't already heard: CVE-2020-7982
While this really doesn't effect us (since MOST packages have to be cross-compiled from source) which makes MITM attacks less than likely. But, I had a setback when i updated the codebase and things broke. Since then, I've been working on finding ways to set the configs up based on the mode. I believe I've got Router mode most of the way done. Anyone actually use Bridge still? or Gateway (which was never finished, i know). IF you use Bridge/Gateway mode as an actual mode, I need to use your configurations. As for Router, I need tests and additions I don't even have Snort running on this yet, but i do have ClamAV and dnsmasq doing their thing Let me know if I should bother continuing to invest time?
Running Itus Shield v2 Firmware
|
|
Hi Grommish Hope your safe and well, since January this year I've been really busy and now been seconded to the police for 2 months collecting dead bodies who have died from the covid 19 virus ( not a nice job but someone has to do it). As for the Shield it's been forgotten because of work but last time it was running the new version which seem to work ok, I would still like to try and test any new versions, as I said before I run in router mode. Keep up the good work. ruodrunneruk On Wed, 8 Apr 2020 at 02:19, Grommish [via Itus Networks Owners Forum] <[hidden email]> wrote: First, in case you hadn't already heard: CVE-2020-7982 |
|
Administrator
|
I know France has been hit hard, be safe.
I have a few big issues to overcome. 1) Initial Setup - something changed in the way the boot process works, so my Firstboot script no longer functions. I've gotten around this, mostly. 2) Snort3 - Snort3 compiles, but I have issues with the Config file, since the config file structure has changed. For whatever reason, it's not also building the tool used to convert a config from Snort2 to Snort3 Lua. 3) Bridge and Gateway Configs - I may not worry about this unless i have someone specifically want to run it and can help with the config. 4) Update system - I'm still working on seeing how I can get the update system to work. All in all, I think the router image is about ready. I'm doing a fresh compile and build and will test it before I upload it.
Running Itus Shield v2 Firmware
|
|
Sorry Grommish, can't offer too much in the way of assistance at the moment. Myself & my wife are both working from home now, so reliable connectivity is a priority - so much so that I've actually switched off our Shield for now due to its tendency to randomly flake out & take me 30+mins each time to sort out. That might coincide with snort rule updates & reboots (?) but snort's the main reason I use it. So whilst I appreciate that you've nearly got Snort3 working, that's a bit of a kicker for me ;-) Let me know if you figure it out! I've actually also recently backed this on Kickstarter: https://www.kickstarter.com/projects/pangolinsecured/pangolin-simple-cybersecurity-for-home-and-small-business. Not expecting it before July now, but I'm hoping it might be a bit more reliable. Unfortunately I don't have the time (or patience ;) to tinker as much as I used to.. On Fri, 10 Apr 2020 at 06:30, Grommish [via Itus Networks Owners Forum] <[hidden email]> wrote: I know France has been hit hard, be safe.
OpenWrt SNAPSHOT, r10391-3d8d528939
|
|
Administrator
|
Oh, I understand :) Just remember me when you move on from the Shield :D
As for the firmware, I'm having a few issues, but nothing insurmountable yet. The biggest issue I have is the fact the Shield uses a mips64 chip. So it means having to fight with and cross-compile everything. I DID get Snort3 working WITH the accompanying tools (including snort2lua!). I had to get LuaJIT to work under mips64 (it won't without help) and then Snort3 itself - but it works. See the pastes below.. During the run, i ran two simultaneous speedtests benchmarks. One from speedtest.googlefiber.net and one from speedtest.net. I never saw above a .50 load or less than 630MB RAM Free. Now, this is running ONLY the very STOCK Snort config! I do NOT know Firewall rules as well as I should, so, who wants to help? *beg* root@OpenWrt:/etc/snort# snort --daq-dir /usr/lib/daq -c /etc/snort/snort.lua -i any -D -------------------------------------------------- o")~ Snort++ 3.0.0-247 -------------------------------------------------- Loading /etc/snort/snort.lua: ips dce_http_proxy wizard pop ftp_server ssl stream_icmp ftp_data dnp3 telnet latency dce_udp imap classifications references binder appid ftp_client smtp gtp_inspect port_scan back_orifice dce_tcp ssh rpc_decode stream_tcp normalizer modbus http2_inspect http_inspect arp_spoof stream_user stream_udp stream_ip stream_file stream dce_http_server dce_smb sip file_id dns Finished /etc/snort/snort.lua. -------------------------------------------------- pcap DAQ configured to passive. initializing daemon mode child process is 2347 Commencing packet processing ++ [0] any root@OpenWrt:/etc/snort# ERROR: Unable to find a Codec with data link type 113 -------------------------------------------------- Packet Statistics -------------------------------------------------- daq received: 2658325 analyzed: 1872001 dropped: 786322 outstanding: 786324 allow: 1872001 idle: 1 rx_bytes: 1970544795 -------------------------------------------------- codec total: 1872001 (100.000%) other: 1872001 (100.000%) -------------------------------------------------- Module Statistics -------------------------------------------------- detection analyzed: 1872001 -------------------------------------------------- latency total_packets: 1872001 total_usecs: 7083213 max_usecs: 8430 packet_timeouts: 44 -------------------------------------------------- Summary Statistics -------------------------------------------------- process signals: 1 -------------------------------------------------- timing runtime: 00:08:32 seconds: 512.525329 packets: 2658325 pkts/sec: 5192 o")~ Snort exiting
Running Itus Shield v2 Firmware
|
|
Can't remember who on the site suggested the setting for snort, but he knew what he was doing, look at the attached files was his changes to speed thing up and things to delete. Here are the modification that I made from his suggestions snort file output alert_fast: alert.fast 64k # output log_tcpdump: tcpdump.log include classification.config include reference.config include reference.config var RULE_PATH /etc/snort/rules/ var PREPROC_RULE_PATH /etc/snort/rules/ var BLACK_LIST_PATH /etc/snort/rules/ include $RULE_PATH/local.rules include $RULE_PATH/snort.rules #include $PREPROC_RULE_PATH/preprocessor.rules #include $PREPROC_RULE_PATH/decoder.rules #include $PREPROC_RULE_PATH/sensitive-data.rules include threshold.conf ipvar HOME_NET 10.10.10.240 ipvar EXTERNAL_NET !$HOME_NET ipvar DNS_SERVERS $HOME_NET ipvar SMTP_SERVERS $HOME_NET ipvar HTTP_SERVERS $HOME_NET ipvar SQL_SERVERS [192.168.0.0/16,10.0.0.0/8,172.16.0.0/12] ipvar TELNET_SERVERS $HOME_NET ipvar SSH_SERVERS $HOME_NET ipvar FTP_SERVERS $HOME_NET ipvar SIP_SERVERS $HOME_NET portvar HTTP_PORTS [36,80,81,82,83,84,85,86,87,88,89,90,311,383,555,591,593,631,801,808,818,901,972,1158,1220,1414,1533,1741,1830,1942,2231,2301,2381,2809,2980,3029,3037,3057,3128,3443,3702,4000,4343,4848,5000,5117,5250,5600,6080,6173,6988,7000,7001,7071,7144,7145,7510,7770,7777,7778,7779,8000,8008,8014,8028,8080,8081,8082,8085,8088,8090,8118,8123,8180,8181,8222,8243,8280,8300,8333,8344,8500,8509,8800,8888,8899,8983,9000,9060,9080,9090,9091,9111,9290,9443,9999,10000,11371,12601,13014,15489,29991,33300,34412,34443,34444,41080,44449,50000,50002,51423,53331,55252,55555,56712] portvar SHELLCODE_PORTS !0 portvar ORACLE_PORTS 1024: portvar SSH_PORTS 22 portvar FTP_PORTS [21,2100,3535] portvar SIP_PORTS [5060,5061,5600] portvar FILE_DATA_PORTS [$HTTP_PORTS,110,143] portvar GTP_PORTS [2123,2152,3386] ipvar AIM_SERVERS [64.12.24.0/23,64.12.28.0/23,64.12.161.0/24,64.12.163.0/24,64.12.200.0/24,205.188.3.0/24,205.188.5.0/24,205.188.7.0/24,205.188.9.0/24,205.188.153.0/24,205.188.179.0/24,205.188.248.0/24] config enable_decode_drops config enable_tcpopt_experimental_drops config enable_tcpopt_obsolete_drops config enable_tcpopt_ttcp_drops config enable_tcpopt_drops config enable_ipopt_drops config enable_decode_oversized_drops config policy_mode:inline config checksum_drop: all #config checksum_mode: all # config flowbits_size: 64 # config ignore_ports: tcp 21 6667:6671 1356 # config ignore_ports: udp 1:17 53 # config response: eth0 attempts 2 config daq: nfq config daq_dir: /usr/lib/daq/ config daq_mode: inline config daq_var: queue=8 #config daq_var: proto=ip6 #config daq_var: queue_len=65535 # config set_gid: # config set_uid: # config snaplen: # config bpf_file: config logdir: /tmp/snort/ config pcre_match_limit: 5000 config pcre_match_limit_recursion: 2500 #config detection: search-method ac search-optimize max-pattern-len 20 config detection: search-method ac-nq split-any-any search-optimize max-pattern-len 20 no_stream_inserts config event_queue: max_queue 8 log 5 order_events content_length # config enable_gtp #config ppm: max-pkt-time 250, \ # fastpath-expensive-packets, \ # pkt-log #config ppm: max-rule-time 200, \ # threshold 3, \ # suspend-expensive-rules, \ # suspend-timeout 20, \ # rule-log alert #config profile_rules: print all, sort avg_ticks #config profile_preprocs: print all, sort avg_ticks config paf_max: 16000 dynamicpreprocessor directory /usr/lib/snort_dynamicpreprocessor/ dynamicengine /usr/lib/snort_dynamicengine/libsf_engine.so #dynamicdetection directory /usr/local/lib/snort_dynamicrules # preprocessor gtp: ports { 2123 3386 2152 } preprocessor normalize_ip4 preprocessor normalize_tcp: ips ecn stream preprocessor normalize_icmp4 preprocessor normalize_ip6 preprocessor normalize_icmp6 preprocessor frag3_global: max_frags 65536 preprocessor frag3_engine: policy windows detect_anomalies overlap_limit 10 min_fragment_length 100 timeout 180 preprocessor stream5_global: track_tcp yes, \ track_udp yes, \ track_icmp yes, \ max_tcp 10000, \ max_udp 10000, \ max_active_responses 2, \ min_response_seconds 5, \ prune_log_max 1120810 preprocessor stream5_tcp: policy windows, detect_anomalies, require_3whs 180, \ overlap_limit 10, small_segments 3 bytes 150, timeout 180, \ max_queued_bytes 1064720, \ ports client 21 22 23 25 42 53 70 79 109 110 111 113 119 135 136 137 139 143 \ 161 445 513 514 587 593 691 1433 1521 1741 2100 3306 6070 6665 6666 6667 6668 6669 \ 7000 8181 32770 32771 32772 32773 32774 32775 32776 32777 32778 32779, \ ports both 36 80 81 82 83 84 85 86 87 88 89 90 110 311 383 443 465 563 555 591 593 631 636 801 808 818 901 972 989 992 993 994 995 1158 1220 1414 1533 1741 1830 1942 2231 2301 2381 2809 2980 3029 3037 3057 3128 3443 3702 4000 4343 4848 5000 5117 5250 5600 6080 6173 6988 7907 7000 7001 7071 7144 7145 7510 7802 7770 7777 7778 7779 \ 7801 7900 7901 7902 7903 7904 7905 7906 7908 7909 7910 7911 7912 7913 7914 7915 7916 \ 7917 7918 7919 7920 8000 8008 8014 8028 8080 8081 8082 8085 8088 8090 8118 8123 8180 8181 8222 8243 8280 8300 8333 8344 8500 8509 8800 8888 8899 8983 9000 9060 9080 9090 9091 9111 9290 9443 9999 10000 11371 12601 13014 15489 29991 33300 34412 34443 34444 41080 44449 50000 50002 51423 53331 55252 55555 56712 preprocessor stream5_udp: timeout 180 # preprocessor perfmonitor: time 300 file /var/snort/snort.stats pktcnt 10000 preprocessor http_inspect: global iis_unicode_map unicode.map 1252 compress_depth 65535 decompress_depth 65535 preprocessor http_inspect_server: server default \ http_methods { GET POST PUT SEARCH MKCOL COPY MOVE LOCK UNLOCK NOTIFY POLL BCOPY BDELETE BMOVE LINK UNLINK OPTIONS HEAD DELETE TRACE TRACK CONNECT SOURCE SUBSCRIBE UNSUBSCRIBE PROPFIND PROPPATCH BPROPFIND BPROPPATCH RPC_CONNECT PROXY_SUCCESS BITS_POST CCM_POST SMS_POST RPC_IN_DATA RPC_OUT_DATA RPC_ECHO_DATA } \ chunk_length 500000 \ server_flow_depth 0 \ client_flow_depth 0 \ post_depth 65495 \ oversize_dir_length 500 \ max_header_length 750 \ max_headers 100 \ max_spaces 200 \ small_chunk_length { 10 5 } \ ports { 36 80 81 82 83 84 85 86 87 88 89 90 311 383 555 591 593 631 801 808 818 901 972 1158 1220 1414 1533 1741 1830 1942 2231 2301 2381 2809 2980 3029 3037 3057 3128 3443 3702 4000 4343 4848 5000 5117 5250 5600 6080 6173 6988 7000 7001 7071 7144 7145 7510 7770 7777 7778 7779 8000 8008 8014 8028 8080 8081 8082 8085 8088 8090 8118 8123 8180 8181 8222 8243 8280 8300 8333 8344 8500 8509 8800 8888 8899 8983 9000 9060 9080 9090 9091 9111 9290 9443 9999 10000 11371 12601 13014 15489 29991 33300 34412 34443 34444 41080 44449 50000 50002 51423 53331 55252 55555 56712 } \ non_rfc_char { 0x00 0x01 0x02 0x03 0x04 0x05 0x06 0x07 } \ enable_cookie \ extended_response_inspection \ inspect_gzip \ normalize_utf \ unlimited_decompress \ normalize_javascript \ apache_whitespace no \ ascii no \ bare_byte no \ directory no \ double_decode no \ iis_backslash no \ iis_delimiter no \ iis_unicode no \ multi_slash no \ utf_8 no \ u_encode yes \ webroot no preprocessor rpc_decode: 111 32770 32771 32772 32773 32774 32775 32776 32777 32778 32779 no_alert_multiple_requests no_alert_large_fragments no_alert_incomplete preprocessor bo preprocessor ftp_telnet: global inspection_type stateful encrypted_traffic no check_encrypted preprocessor ftp_telnet_protocol: telnet \ ayt_attack_thresh 20 \ normalize ports { 23 } \ detect_anomalies preprocessor ftp_telnet_protocol: ftp server default \ def_max_param_len 100 \ ports { 21 2100 3535 } \ telnet_cmds yes \ ignore_telnet_erase_cmds yes \ ftp_cmds { ABOR ACCT ADAT ALLO APPE AUTH CCC CDUP } \ ftp_cmds { CEL CLNT CMD CONF CWD DELE ENC EPRT } \ ftp_cmds { EPSV ESTA ESTP FEAT HELP LANG LIST LPRT } \ ftp_cmds { LPSV MACB MAIL MDTM MIC MKD MLSD MLST } \ ftp_cmds { MODE NLST NOOP OPTS PASS PASV PBSZ PORT } \ ftp_cmds { PROT PWD QUIT REIN REST RETR RMD RNFR } \ ftp_cmds { RNTO SDUP SITE SIZE SMNT STAT STOR STOU } \ ftp_cmds { STRU SYST TEST TYPE USER XCUP XCRC XCWD } \ ftp_cmds { XMAS XMD5 XMKD XPWD XRCP XRMD XRSQ XSEM } \ ftp_cmds { XSEN XSHA1 XSHA256 } \ alt_max_param_len 0 { ABOR CCC CDUP ESTA FEAT LPSV NOOP PASV PWD QUIT REIN STOU SYST XCUP XPWD } \ alt_max_param_len 200 { ALLO APPE CMD HELP NLST RETR RNFR STOR STOU XMKD } \ alt_max_param_len 256 { CWD RNTO } \ alt_max_param_len 400 { PORT } \ alt_max_param_len 512 { SIZE } \ chk_str_fmt { ACCT ADAT ALLO APPE AUTH CEL CLNT CMD } \ chk_str_fmt { CONF CWD DELE ENC EPRT EPSV ESTP HELP } \ chk_str_fmt { LANG LIST LPRT MACB MAIL MDTM MIC MKD } \ chk_str_fmt { MLSD MLST MODE NLST OPTS PASS PBSZ PORT } \ chk_str_fmt { PROT REST RETR RMD RNFR RNTO SDUP SITE } \ chk_str_fmt { SIZE SMNT STAT STOR STRU TEST TYPE USER } \ chk_str_fmt { XCRC XCWD XMAS XMD5 XMKD XRCP XRMD XRSQ } \ chk_str_fmt { XSEM XSEN XSHA1 XSHA256 } \ cmd_validity ALLO < int [ char R int ] > \ cmd_validity EPSV < [ { char 12 | char A char L char L } ] > \ cmd_validity MACB < string > \ cmd_validity MDTM < [ date nnnnnnnnnnnnnn[.n[n[n]]] ] string > \ cmd_validity MODE < char ASBCZ > \ cmd_validity PORT < host_port > \ cmd_validity PROT < char CSEP > \ cmd_validity STRU < char FRPO [ string ] > \ cmd_validity TYPE < { char AE [ char NTC ] | char I | char L [ number ] } > preprocessor ftp_telnet_protocol: ftp client default \ max_resp_len 256 \ bounce yes \ ignore_telnet_erase_cmds yes \ telnet_cmds yes #preprocessor smtp: ports { 25 465 587 691 } \ # inspection_type stateful \ # b64_decode_depth 0 \ # qp_decode_depth 0 \ # bitenc_decode_depth 0 \ # uu_decode_depth 0 \ # log_mailfrom \ # log_rcptto \ # log_filename \ # log_email_hdrs \ # normalize cmds \ # normalize_cmds { ATRN AUTH BDAT CHUNKING DATA DEBUG EHLO EMAL ESAM ESND ESOM ETRN EVFY } \ # normalize_cmds { EXPN HELO HELP IDENT MAIL NOOP ONEX QUEU QUIT RCPT RSET SAML SEND SOML } \ # normalize_cmds { STARTTLS TICK TIME TURN TURNME VERB VRFY X-ADAT X-DRCP X-ERCP X-EXCH50 } \ # normalize_cmds { X-EXPS X-LINK2STATE XADR XAUTH XCIR XEXCH50 XGEN XLICENSE XQUE XSTA XTRN XUSR } \ # max_command_line_len 512 \ # max_header_line_len 1000 \ # max_response_line_len 512 \ # alt_max_command_line_len 260 { MAIL } \ # alt_max_command_line_len 300 { RCPT } \ # alt_max_command_line_len 500 { HELP HELO ETRN EHLO } \ # alt_max_command_line_len 255 { EXPN VRFY ATRN SIZE BDAT DEBUG EMAL ESAM ESND ESOM EVFY IDENT NOOP RSET } \ # alt_max_command_line_len 246 { SEND SAML SOML AUTH TURN ETRN DATA RSET QUIT ONEX QUEU STARTTLS TICK TIME TURNME VERB X-EXPS X-LINK2STATE XADR XAUTH XCIR XEXCH50 XGEN XLICENSE XQUE XSTA XTRN XUSR } \ # valid_cmds { ATRN AUTH BDAT CHUNKING DATA DEBUG EHLO EMAL ESAM ESND ESOM ETRN EVFY } \ # valid_cmds { EXPN HELO HELP IDENT MAIL NOOP ONEX QUEU QUIT RCPT RSET SAML SEND SOML } \ # valid_cmds { STARTTLS TICK TIME TURN TURNME VERB VRFY X-ADAT X-DRCP X-ERCP X-EXCH50 } \ # valid_cmds { X-EXPS X-LINK2STATE XADR XAUTH XCIR XEXCH50 XGEN XLICENSE XQUE XSTA XTRN XUSR } \ # xlink2state { enabled } preprocessor sfportscan: proto { all } memcap { 500000 } sense_level { medium } # preprocessor arpspoof # preprocessor arpspoof_detect_host: 192.168.40.1 f0:0f:00:f0:0f:00 preprocessor ssh: server_ports { 22 } \ autodetect \ max_client_bytes 19600 \ max_encrypted_packets 20 \ max_server_version_len 100 \ enable_respoverflow enable_ssh1crc32 \ enable_srvoverflow enable_protomismatch preprocessor dcerpc2: memcap 102400, events [co ] preprocessor dcerpc2_server: default, policy WinXP, \ detect [smb [139,445], tcp 135, udp 135, rpc-over-http-server 593], \ autodetect [tcp 1025:, udp 1025:, rpc-over-http-server 1025:], \ smb_max_chain 3, smb_invalid_shares ["C$", "D$", "ADMIN$"] preprocessor dns: ports { 53 } enable_rdata_overflow preprocessor ssl: ports { 443 465 563 636 989 992 993 994 995 7801 7802 7900 7901 7902 7903 7904 7905 7906 7907 7908 7909 7910 7911 7912 7913 7914 7915 7916 7917 7918 7919 7920 }, trustservers, noinspect_encrypted #preprocessor sensitive_data: alert_threshold 25 #preprocessor sip: max_sessions 1024, \ # ports { 5060 5061 5600 }, \ # methods { invite \ # cancel \ # ack \ # bye \ # register \ # options \ # refer \ # subscribe \ # update \ # join \ # info \ # message \ # notify \ # benotify \ # do \ # qauth \ # sprack \ # publish \ # service \ # unsubscribe \ # prack }, \ # max_uri_len 512, \ # max_call_id_len 80, \ # max_requestName_len 20, \ # max_from_len 256, \ # max_to_len 256, \ # max_via_len 1024, \ # max_contact_len 512, \ # max_content_len 2048 #preprocessor imap: \ # ports { 143 } \ # b64_decode_depth 0 \ # qp_decode_depth 0 \ # bitenc_decode_depth 0 \ # uu_decode_depth 0 #preprocessor pop: \ # ports { 110 } \ # b64_decode_depth 0 \ # qp_decode_depth 0 \ # bitenc_decode_depth 0 \ # uu_decode_depth 0 #preprocessor modbus: ports { 502 } #preprocessor dnp3: ports { 20000 } \ # memcap 131077 \ # check_crc #preprocessor reputation: \ # memcap 100, \ # priority whitelist, \ # nested_ip inner, \ # whitelist $WHITE_LIST_PATH/white_list.rules, \ # blacklist $BLACK_LIST_PATH/L2.blacklist # output unified2: filename merged.log, limit 128, nostamp, mpls_event_types, vlan_event_types # output alert_unified2: filename snort.alert, limit 128, nostamp # output log_unified2: filename snort.log, limit 128, nostamp On Sun, 12 Apr 2020 at 04:45, Grommish [via Itus Networks Owners Forum] <[hidden email]> wrote: Oh, I understand :) Just remember me when you move on from the Shield :D |
|
Administrator
|
Thanks! I'll take a look.
I'm having to learn the new format, which is slowing me down. This is the "new" Snort3 config format. The entire system has changed and what it can or should do.. I'm going to get it stable and running on the vanilla configuration. I'm then going to put up a test image that can go in the Gateway position, but act as a router... That way, anyone who wants to test can do so without touching the production (router or bridge) setting... Should make it easier for those who don't have a lot of time to play without having to worry about trashing what already works.
Running Itus Shield v2 Firmware
|
|
Administrator
|
Ok, so.. I think I finally have a grip on this.. OpenWrt has MANY cool systems when you're building from scratch, but they are just a huge pain to find.
I found reference to the /etc/uci-defaults directory, which will run a file on the first boot, then delete it. This allows me to do selective settings via the uci! I have abandoned using ClamAV in the image. It's huge and resource heavy, and not really useful given what would have to be given up for it (like.. Snort..or Adblock..) ClamAV has an 800MB RAM footprint! So.. Ah well.
Running Itus Shield v2 Firmware
|
|
Administrator
|
Itus Shield Firmware v2.0 (OpenWrt SNAPSHOT r11407+1525-54ba15f9fa) ALPHA
NOTE: This WILL erase ALL DATA in the GATEWAY slot! Download ItusgatewayImage 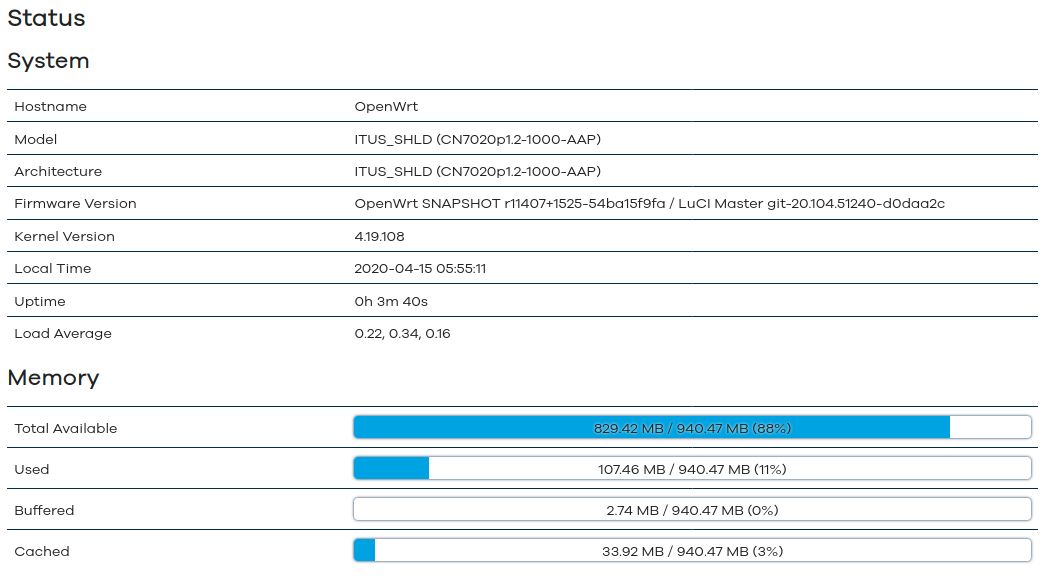 Instructions to Flash: Boot into the Shield in whatever mode that you normally use If you have ssh/scp installed on your PC, you can use it directly. MAKE SURE YOU ARE IN THE DIRECTORY YOU DOWNLOADED THE FILE INTO! ssh -q -o StrictHostKeyChecking=no -o UserKnownHostsFile=/dev/null root@10.10.10.10 "mount /dev/mmcblk0p1 /overlay" ssh -q -o StrictHostKeyChecking=no -o UserKnownHostsFile=/dev/null root@10.10.10.10 "cp /overlay/ItusgatewayImage /overlay/ItusgatewayImage-Rescue" scp -o StrictHostKeyChecking=no -o UserKnownHostsFile=/dev/null ./ItusgatewayImage root@10.10.10.10:/overlay ssh -q -o StrictHostKeyChecking=no -o UserKnownHostsFile=/dev/null root@10.10.10.10 "touch /overlay/ItusgatewayImage" ssh -q -o StrictHostKeyChecking=no -o UserKnownHostsFile=/dev/null root@10.10.10.10 "umount /overlay" (the flags above just keep SSH/SCP from complaining about the SSH Key for your Shield if it changed. This way, you don't have to remove the key and re-add a new one) You MUST ensure that your Shield is in the GATEWAY (OUTER) Position, then reboot First boot will take a few minutes. The M-LED on the Shield will turn ORANGE when the boot is complete. Open 10.10.10.10 and login (no password by default) Troubleshooting: If you boot into the new image and you have no IP on eth0: This happens from time to time, and I'm not sure why. Reboot the system and let it try again. Requests: Suggested changes to the "default" setup are welcome.. Packages, settings, etc.
Running Itus Shield v2 Firmware
|
|
In reply to this post by Grommish
Great work can't wait for new build. On Wed, 15 Apr 2020 at 06:46, Grommish [via Itus Networks Owners Forum] <[hidden email]> wrote: Ok, so.. I think I finally have a grip on this.. OpenWrt has MANY cool systems when you're building from scratch, but they are just a huge pain to find. |
«
Return to Technical Discussion
|
1 view|%1 views
| Free forum by Nabble | Edit this page |

