[FIRMWARE] Itus Networks Shield Firmware Upgrade *WIP*
1 ...
45678910
... 12

1 ...
45678910
... 12
|
Sorry gents, first thing in the morning over here now.. Yep, different base images will explain things. I will add some checks for pre-existing snort.rules and L2.blacklist files before trying to rename them *.bak Also, if I've based paths on suricata ones and there are better vanilla snort ones to use, let me know! On Sun, 18 Aug. 2019, 4:18 am Grommish [via Itus Networks Owners Forum], <[hidden email]> wrote: Ok.. Road/Gnomad, try this image.
OpenWrt SNAPSHOT, r10391-3d8d528939
|
|
Administrator
|
I've already corrected the image to fit your script, so nothing should need to be changed on your end. That snort.tgz file was creating some of the directory structure when it built out first boot. With that gone, it stopped creating them 😀 Anyway, it's fixed now if you want to check out the new image, and double check that it works. Just copy the image over to /dev/mmcblk1p1 and remove /.norwits then reboot and it'll clear out the old partition and rebuild from the image On Sat, Aug 17, 2019, 9:14 PM Gnomad [via Itus Networks Owners Forum] <[hidden email]> wrote:
Running Itus Shield v2 Firmware
|
|
Administrator
|
The advantage to me being Eastern US time is that I have time while you sleep to get things done.. Besides, it takes almost no time to compile this on my laptop, unless I'm doing a kernel change or removing a dependency and have to do a make clean. Otherwise, it literally takes about a minute and a half.
As far as Suricata goes, Suricata 5 will REQUIRE Rust and Cargo to compile and run. Unfortunately, Rust does not have a mips compatible source code (at least, not yet). I was able to get Suricata 4.1.4 to build once I finagled it, but abandoned the task once I started looking into the requirements for the current Beta. If they ever update it, then I'll go back to it. So, for now, we can put them where-ever we want.. Even if Suracata comes back to the Shield down the line, we can make the structure however. Itus used the "profiles" directly to hold the Suricata AND Snort configs, and I wasn't even aware Suricata was an option.. You can see tags for it in the LUA page for IDS on the original Shield files. I don't know if they ever included Suricata or not, but it's the whole reason we have a profile directory at all. I didn't understand at the beginning what they were using profiles for, so I just dropped it to profile and stored my config files for Snort in there so they could be cat'ed when the service starts into snort.conf (and edited in pieces from luCi)
Running Itus Shield v2 Firmware
|
|
In reply to this post by Grommish
Whoah - new theme! :)
Yes I can confirm that works nicely. Apologies for the mixup deleting snort.tar.gz. I figured files under /files would be unpacked to track changes, so had assumed the .tar was a leftover. On the console updaterules.sh will complain about no initial snort.rules and L2.blacklist files on first run only, but that doesn't stop it doing its thing. Subsequent runs it doesn't complain. 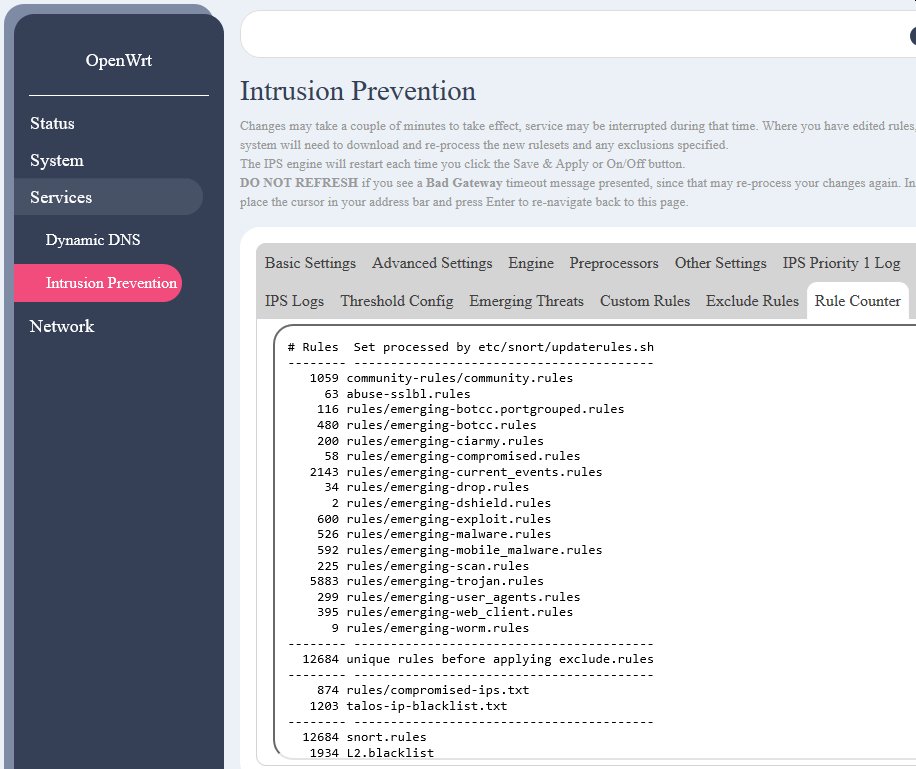 PS: don't see any 404s but the serif font looks a little funny - might be missing a font replacement?
OpenWrt SNAPSHOT, r10391-3d8d528939
|
|
Administrator
|
No worries on the tgz. The original plan was to house complete snort configurations, and other configs, in one of three tgz files and unpack it at first boot depending on which mode the Shield was in (by reading the switch GPIOs) That way, we only really have to maintain a single image and put things like network configs, snort configs, e2guardian configs in the tgz files where they differ from router to bridge to Gateway. And I included 3 additional luCi themes in the image, besides the default On Sat, Aug 17, 2019, 9:51 PM Gnomad [via Itus Networks Owners Forum] <[hidden email]> wrote: Whoah - new theme! :)
Running Itus Shield v2 Firmware
|
|
In reply to this post by Roadrunnere42
Btw cheers for the compliment @Roadrunner, but you (& Hans, user8446 etc) did all the heavy lifting!
I just based it all from your fw_upgrade and got the benefit of slapping Grommish's v2 label on it ;) Note, I'm not having any problems with heat or throughput with the case on - all seems pretty solid so far..
OpenWrt SNAPSHOT, r10391-3d8d528939
|
Re: [FIRMWARE] Itus Networks Shield Firmware Upgrade *WIP*
|
In reply to this post by Grommish
All working fine Been playing around and maybe you want to change this file in /etc/config/hhttpd to prevent uhttpd listing on the wan port, they also say unbind ipv6 but couldn't fine any reference in uhttpd. I will make suggestion as i play and let you full time computer guys decide what to include, Im just a guy who likes computers with no programming knowledge, just picking things up as i go Securing uHTTPd
By default, uHTTPd is bind to To get your current LAN IP address run this command: root@OpenWrt:~# uci get network.lan.ipaddr 10.10.10.10
Then edit config uhttpd main
# HTTP listen addresses, multiple allowed
list listen_http 10.10.10.10:80
# list listen_http [::]:80
# HTTPS listen addresses, multiple allowed
list listen_https 10.10.10.10:443
# list listen_https [::]:443
On Sat, 17 Aug 2019 at 16:34, Grommish [via Itus Networks Owners Forum] <[hidden email]> wrote:
|
|
Administrator
|
Added.. I can't see a downside except for potentially not being able to access luCi from the outside for those who need it.. But, You'd expect someone needing to do that would have VPN, so I'm good with the change.
Running Itus Shield v2 Firmware
|
|
Administrator
|
As a small update, I've put in a script that automates the process of black-listing URLs (rather than IP addresses). Ideally, it is used as an ad-hoc ad-blocker.
Anyone feel like creating a luCi page for it? Let me know and I can give you details since I've not pushed it to GH yet.
Running Itus Shield v2 Firmware
|
|
Can do, flick me the deets.
Domains blocked via snort or e2guardian? We could maybe add the ability to update via published ad lists like those at https://filterlists.com..
OpenWrt SNAPSHOT, r10391-3d8d528939
|
|
Administrator
|
Even better and more reliable. I used the local /etc/hosts file to void out specific urls. The lists are maintained, but any URL list should work. I'll put a commit up shortly I hope On Mon, Sep 2, 2019, 6:15 AM Gnomad [via Itus Networks Owners Forum] <[hidden email]> wrote: Can do, flick me the deets.
Running Itus Shield v2 Firmware
|
|
Administrator
|
I have this as /etc/snort/updateblacklist.sh
|
|
Administrator
|
I have a concern that I need help addressing with the update script.
1) We are pulling these from external sources 2) The update lists can contain anything We need to see if there is a way to ENSURE anything added via the update script points to 0.0.0.0 or 127.0.0.1 so if the external source gets poisoned, we aren't effected by a DNS attack. So, we gotta figure out a way to do it. Suggestions? Gnomad, you might be able to to come up with something script wise?
Running Itus Shield v2 Firmware
|
|
That script doesn't quite work on my Shield as-is - not sure if you had to make any edits?
I guess we're after a lua page with an on/off switch, plus potential replacement of the master list URL. Will have a bit of a play, also see if I can swing some `sed` filtering to strip any invalid localhost IPs.
OpenWrt SNAPSHOT, r10391-3d8d528939
|
|
Administrator
|
Hmm.
This is my output, and I'll repost the script. What is line 45 on you end? Mine is a for loop.
/etc/snort/updateblacklist.sh
Running Itus Shield v2 Firmware
|
|
All good once I `chmod`ed it to execute via `./updateblacklist.sh` as you did - not sure why it made a difference, but hey. On Sun, 8 Sep 2019 at 14:16, Grommish [via Itus Networks Owners Forum] <[hidden email]> wrote: Hmm.
OpenWrt SNAPSHOT, r10391-3d8d528939
|
|
In reply to this post by Gnomad
PR up for a "safe" /etc/snort/hosts/updatehosts.sh
https://github.com/Grommish/Itus_Shield_v2/pull/2/files#diff-f363d9f8c5abce896b52b3f2a5df9b3e But 1. although pinging from the Shield directly resolves to 127.0.0.1 as expected, browsing to these domains from a downstream client is not blocked. I guess we need to change client DNS to the Shield? 2. local speedtest was then 60% slower than before. I brought this back up to reasonable speeds by commenting out the larger https://hosts-file.net/emd.txt and psh.txt downloads. I wonder if e2guardian might perform better, obviate the need to change client DNS entries?
root@OpenWrt:/# /etc/snort/hosts/updatehosts.sh
Preparing working directory for host list download and ingestion
/tmp/hosts
Downloading bad host list urls from https://v.firebog.net/hosts/lists.php?type=tick
...
908683 badhosts.all
Sorting bad hosts and removing duplicates
Cleaning up working files
Displaying host_counter.log
# Hosts Url processed by etc/snort/hosts/updatehosts.sh
-------- -----------------------------------------------
526 https://hosts-file.net/grm.txt
713 https://reddestdream.github.io/Projects/MinimalHosts/etc/MinimalHostsBlocker/minimalhosts
3619 https://raw.githubusercontent.com/StevenBlack/hosts/master/data/KADhosts/hosts
73 https://raw.githubusercontent.com/StevenBlack/hosts/master/data/add.Spam/hosts
753 https://v.firebog.net/hosts/static/w3kbl.txt
411 https://adaway.org/hosts.txt
29855 https://v.firebog.net/hosts/AdguardDNS.txt
34374 https://raw.githubusercontent.com/anudeepND/blacklist/master/adservers.txt
2703 https://s3.amazonaws.com/lists.disconnect.me/simple_ad.txt
45739 https://hosts-file.net/ad_servers.txt
1609 https://v.firebog.net/hosts/Easylist.txt
3039 https://pgl.yoyo.org/adservers/serverlist.php?hostformat=hosts;showintro=0
10 https://raw.githubusercontent.com/StevenBlack/hosts/master/data/UncheckyAds/hosts
4315 https://www.squidblacklist.org/downloads/dg-ads.acl
2766 https://v.firebog.net/hosts/Easyprivacy.txt
3634 https://v.firebog.net/hosts/Prigent-Ads.txt
14467 https://gitlab.com/quidsup/notrack-blocklists/raw/master/notrack-blocklist.txt
1286 https://raw.githubusercontent.com/StevenBlack/hosts/master/data/add.2o7Net/hosts
367 https://raw.githubusercontent.com/crazy-max/WindowsSpyBlocker/master/data/hosts/spy.txt
2738 https://s3.amazonaws.com/lists.disconnect.me/simple_malvertising.txt
26886 https://mirror1.malwaredomains.com/files/justdomains
1158 https://hosts-file.net/exp.txt
300351 https://hosts-file.net/emd.txt
189142 https://hosts-file.net/psh.txt
3202 https://mirror.cedia.org.ec/malwaredomains/immortal_domains.txt
1106 https://www.malwaredomainlist.com/hostslist/hosts.txt
2046 https://bitbucket.org/ethanr/dns-blacklists/raw/8575c9f96e5b4a1308f2f12394abd86d0927a4a0/bad_lists/Mandiant_APT1_Report_Appendix_D.txt
6785 https://v.firebog.net/hosts/Prigent-Malware.txt
6785 https://v.firebog.net/hosts/Prigent-Phishing.txt
1533 https://phishing.army/download/phishing_army_blocklist_extended.txt
155 https://gitlab.com/quidsup/notrack-blocklists/raw/master/notrack-malware.txt
1902 https://ransomwaretracker.abuse.ch/downloads/RW_DOMBL.txt
219 https://ransomwaretracker.abuse.ch/downloads/CW_C2_DOMBL.txt
214 https://ransomwaretracker.abuse.ch/downloads/LY_C2_DOMBL.txt
144 https://ransomwaretracker.abuse.ch/downloads/TC_C2_DOMBL.txt
33 https://ransomwaretracker.abuse.ch/downloads/TL_C2_DOMBL.txt
19570 https://v.firebog.net/hosts/Shalla-mal.txt
2580 https://raw.githubusercontent.com/StevenBlack/hosts/master/data/add.Risk/hosts
165519 https://www.squidblacklist.org/downloads/dg-malicious.acl
26364 https://zerodot1.gitlab.io/CoinBlockerLists/hosts
-------- -----------------------------------------------
745135 unique bad hosts
Using host template defined at /etc/snort/hosts/hosts
Appending badhosts
Replacing /etc/hosts
Restarting network
OpenWrt SNAPSHOT, r10391-3d8d528939
|
|
Administrator
|
I've not noticed a performance hit, but I've been tearing my network up here recently, so it wouldn't surprise me.
Does e2Guardian handle URL blacklisting or just content type blacklisting? I've not used it. Interesting about the clients being able to connect, because when I originally had the YouTube stuff in there (since removed), YouTube would freak out and tell me I'm offline when it tried (and failed) to load an ad.. Dunno. I say we call this is a serious work in progress, and look into the e2 suggestion.. If nothing else, we could probably modify the fixed script to update e2. The original concept for this was from a project called PiHole, which used a Raspberry Pi as a DNS server to blacklist. Think of it as a poor-man's Shield. They didn't have mips support for the program itself, so I pulled the update streams to see if it could be adapted.
Running Itus Shield v2 Firmware
|
|
Administrator
|
I wonder if we could get dnsmasq to do what we need it to do. Maybe it should be in there and the /etc/hosts?
Running Itus Shield v2 Firmware
|
|
You're probably right re: dnsmasq, but my experience doesn't extend to much network admin.. If we can get these redirecting to the 10.10.10.11 "badhost" http server that the other images have, we also might be able to prevent Youtube thinking that the adservers are disconnected? On Mon, 16 Sep 2019 at 13:19, Grommish [via Itus Networks Owners Forum] <[hidden email]> wrote: I wonder if we could get dnsmasq to do what we need it to do. Maybe it should be in there and the /etc/hosts?
OpenWrt SNAPSHOT, r10391-3d8d528939
|
«
Return to Technical Discussion
|
1 view|%1 views
| Free forum by Nabble | Edit this page |


