[FIRMWARE] Itus Networks Shield Firmware Upgrade *WIP*
1234567
... 12
1234567
... 12
|
Administrator
|
If you ever want to test the image, let me know! It's easier to make changes on-device I've found. I cheat a little and make some changes to my source tree and scp them to the Shield. This way, I can use nano and make sure any changes I do make is tracked by git.
nano IS baked into the image, but I'm using minicom to the console because puTTy for linux doesn't have a reliable cut/paste system (I'm on a laptop, so my touchpad doesn't have a "middle" button for pasting). On the terminal and minicom, i can just use vi and cntl-shift-c/v
Running Itus Shield v2 Firmware
|
|
Appreciate that, just a matter of not enough time outside work at the minute, plus a different project taking up the little I have.. I promise if that eases up I'll hit you up for the latest image & instructions - I know where you live ;) (i.e., this thread!) On Tue, 2 Jul 2019 at 15:26, Grommish [via Itus Networks Owners Forum] <[hidden email]> wrote: If you ever want to test the image, let me know! It's easier to make changes on-device I've found. I cheat a little and make some changes to my source tree and scp them to the Shield. This way, I can use nano and make sure any changes I do make is tracked by git.
OpenWrt SNAPSHOT, r10391-3d8d528939
|
|
Administrator
|
I hear you, Gnomad. i know how it can be!
Just as a quick update, I did confirm that luCi has crontab pages built in, although it was a pain to find... It's listed a "Scheduled Tasks" under System. I can say that moving anything from the original Itus luCi over is very simple. It's just a matter of putting the entry in the Controller director and then dropping the lua page itself in the tree.. So, if there is anything else you can think that might be nice to have, let me know! I did remove/not put back in the Itus "Advanced" mode. I saw it as simply a waste of time hiding the real settings.
Running Itus Shield v2 Firmware
|
|
Administrator
|
Quick update.
I've gotten Suricata 4.1.4 to build! OpenWrt doesn't support it, so I'm in fairly uncharted territory. I'm having issues RUNNING it, but it seems to be a configuration issue rather than a compile issue. Aside from that, I'm also in the process of starting a business, so my time for building will be reduced as I get the systems built out for other things. It is certainly still going forward. I've recently put the case back on the Shield, and then started getting weird issues.. All of the sudden, DNS would go away. Granted, I was maxing out my bandwidth for HOURS on end (I tracked 1TB down on one machine in about 24 hours - all of which ran through the Shield). I don't know if it's a heat issue, a memory issue, or what.. With Snort running, I was cull'ing the logs every 30 minutes, but given the rate at which 1MB logs form, it might not have survived the 30 minute time span without filling up RAM, so I'm running it every 10 minutes now. Or.. it could be a heat issue. The top of the case (Where the word Shield is) is temp'ing out at 103*F, so you know it's hotter internally. I never could find a 5vDC fan to hook to the stub on the PCB that would work, so it's just the copper heatsink. If it continues, I'll pull the cover off again and see what happens..
Running Itus Shield v2 Firmware
|
|
Administrator
|
I've been stress testing the Shield here recently while using Snort (Suricata is still being a pain).
I'm pretty happy with the results. It's been really rock steady so far.
Running Itus Shield v2 Firmware
|
|
Administrator
|
Suricata 4.1.4 works! So, it'll be an option if anyone wants to use it over Snort. Now I get the fun job of trying to learn another IPS/IDS system and how it works... yay...
I'm also going to enable DoH (DNS over HTTPS) by default, unless someone can give me a reason NOT to.. I see it as a security issue that should be addressed. Anyone have any thoughts on it?
Running Itus Shield v2 Firmware
|
|
Nice one Grommish, enjoying watching the progress you’re making in this, just wanted to let you know we’re listening, even if some of us can’t contribute per se. Must admit my 2 shields haven’t seen action for over a year since I switched to sophos utm but now looking forward to the possibility of bringing the shield back online! Thanks for your efforts.
Running v2 Firmware
|
|
Administrator
|
I appreciate the comments.
I think I'm going to have to shelve the Suricata package for now. While 4.1.4 works, the current 5.0.0-beta1 is going to result in a change to Suricata that requires rust-lang and cargo. I've been talking with the Suricata dev team about it, and we are working through it. I don't mind having rust-lang and cargo on the build machine, and we are trying to figure out if rustc and cargo are used AFTER the compile or not. However, it may be a moot point given the fact that as far as I can tell, the rust lang isn't mips64 compatible (yet?). Dunno. I'll leave it as an option for 4.1.4, but I'm not sure if it'll be able to be upgraded in the future. Aside from that issue, unless I get suggestions/comments on what else can/should be included by default (remember, opkg works and will allow each user to install things they want on top of the base image), then I'm going to close it out and begin the process of organizing, cleanup, and finalizing the image. Todo List: - Redo/Finalize Firstboot process - Define Shield mode configuration requirements (Router/Gateway/Bridge) -- Set network configs -- Set snort configs - Verify e2guardian settings - Create snort update script -- On this point, I need suggestions on where to get the rules from (if different from the previous suggested ones) - Figure out the Firmware update system to allow delta tar file updates through luCi interface -- This sort of works now, but reports an error and requires a forced update (unacceptable) - Remove various debugging /dev/kmsg messages
Running Itus Shield v2 Firmware
|
|
Administrator
|
Just a quick message update.
I've not forgotten about things here, but my time has become limited in what I can do code wise. So, for now, I'm still working on it, but it's going to be slow.
Running Itus Shield v2 Firmware
|
|
Shout out @Grommish - thank you and well done for your efforts!!
With your new image and help to install, I'm now running updated OpenWrt in router mode  Top priorities I see are figuring out how to improve the initial reliability of ETH0 on boot, and configuring Snort - I know we've had *many* iterations since the original ~19,000 Itus rules, so maybe we can lean on some @user8446 and others' expertise if we can convince them to give this a whirl too - the new version is a little different to the old, and I was never particularly familiar with it.. ;) I've seen the box spontaneously reboot itself once during a speedtest, but I'll keep it running & let you know re: stability over the next while. I've kept my Shield case ON, which may affect heat - but will be good to see either way.
BusyBox v1.31.0 () built-in shell (ash)
_______ ________ __
| |.-----.-----.-----.| | | |.----.| |_
| - || _ | -__| || | | || _|| _|
|_______|| __|_____|__|__||________||__| |____|
|__| W I R E L E S S F R E E D O M
-----------------------------------------------------
OpenWrt SNAPSHOT, r10391-3d8d528939
-----------------------------------------------------
root@Shield:/# ps | grep snort
1387 root 539m S /usr/bin/snort -Q -q -i br-lan:eth0 -c /etc/snort/sn
1736 root 1528 S grep snort
root@Shield:/# speedtest
Download: 48.49 Mbit/s
OpenWrt SNAPSHOT, r10391-3d8d528939
|
|
Administrator
|
Thanks!
I've never seen a spontaneous reboot, but if it is a heat issue, it could manifest in many ways. If you can swing it, maybe keep the console open and in the background logging the output. That way, if it does it again, maybe we can see a log of it. Updating Snort rules is easy enough for the rules themselves, but the issue will be 1) where to pull updates from and 2) learning sed enough to script a change from ALERT to DROP (I'm sure I can find a workable example online to do what I need it to do). Aside from that, it's just a matter of working out the list I outlined previously. Importantly, getting the update system to work, otherwise we end up losing changes because we have to reflash and rebuild the partition for each upgrade. Changes you make will stick around, @Gnomad, so play around and anything good you hit on, let me know and I can bake it in (scripts, config changes, etc) Hit me up if you need help finding something and I'll do my best to find it in the system.
Running Itus Shield v2 Firmware
|
|
Administrator
|
I should mention:
Snort configuration is handled in the /etc/snort/profile/ directory (config1, config2, etc). Changes made to the files in there are combined into /etc/snort/snort.conf when the service starts. So, if you want to make changes to Snort, do it in those files and then do a services snort restart, it'll combine and start.
|
|
This post was updated on .
Cool, so propose this as a reasonable way to track changes?
a. fork your repo b. baseline these files under the /files/etc/snort/profile folder c. PR changes back to you (I presume content under /files is just pasted over the top once the image is restored?) On Mon, 5 Aug 2019 at 01:22, Grommish [via Itus Networks Owners Forum] < ml+s77436n1807h41@n6.nabble.com> wrote: > I should mention: > > Snort configuration is handled in the /etc/snort/profile/ directory > (config1, config2, etc). Changes made to the files in there are combined > into /etc/snort/snort.conf when the service starts. So, if you want to > make changes to Snort, do it in those files and then do a services snort > restart, it'll combine and start. > > > config1_advanced.conf config3_preprocessors.conf > config2_engine.conf config4_other.conf > root@OpenWrt:/etc/snort/profile# > Ideally, in luCI under Intrusion Prevention, the Advanced Settings, > Engine, Preprocessor, Other Settings, and Threshold tabs are where you'd > make your changes, but I usually use vim in console myself. > Running Itus Shield v2 Firmware > > > ------------------------------ > If you reply to this email, your message will be added to the discussion > below: > > http://itus.accessinnov.com/FIRMWARE-Itus-Networks-Shield-Firmware-Upgrade-WIP-tp1726p1807.html > To unsubscribe from [FIRMWARE] Itus Networks Shield Firmware Upgrade > *WIP*, click here > <http://itus.accessinnov.com/template/NamlServlet.jtp?macro=unsubscribe_by_code&node=1726&code=Y29udGFjdEBnbm9tYWQuaW5mb3wxNzI2fC04ODUxOTI3Mjg=> > . > NAML > <http://itus.accessinnov.com/template/NamlServlet.jtp?macro=macro_viewer&id=instant_html%21nabble%3Aemail.naml&base=nabble.naml.namespaces.BasicNamespace-nabble.view.web.template.NabbleNamespace-nabble.view.web.template.NodeNamespace&breadcrumbs=notify_subscribers%21nabble%3Aemail.naml-instant_emails%21nabble%3Aemail.naml-send_instant_email%21nabble%3Aemail.naml> >
OpenWrt SNAPSHOT, r10391-3d8d528939
|
|
Administrator
|
You can fork the repo if you want, but realistically, it's bigger than you need unless you plan on trying to build our an image yourself. The only thing that would cause issues with building your own image is that I didn't keep track of the host package requirements. So, you'd have to build out the image and when it errors, add the required package to your system, build out again.. Wash, rinse, repeat until it builds out.
Optionally, you can make the changes on your Shield device and once you're happy with the changes, you can send me the changed files directly, put them here, or git init your own repo on GitHub for just the Snort directory (or /etc) and I can cherry pick the changes from it. However you want to do it, and whatever is easiest for you. I can make it work in any of the above situations. The /files folder are files that are included (in the file structure outlined) in the image when it's compiled, yes. It's how I add custom files outside of the vanilla stock version unless I have to specifically edit a package itself (which is why I use https://github.com/Grommish/OpenWrt_Feeds_Packages for that, so I can merge my changes with commits from the upstream).
Running Itus Shield v2 Firmware
|
|
Cool, having a bit of a play, getting my head back in the space.. I noticed the old rc.local had a fair bit of custom stuff in there re: restarting network interfaces, etc. Don't know if some of this might be useful in getting around those occasional issues after boot? https://github.com/ItusShield/Shield-Master/blob/master/etc/rc.local Some of the interface changes are performance related, came from http://itus.accessinnov.com/More-improvements-and-bugfixes-for-the-shield-td1228.html In this thread also, recommended changes to snort config detection, removal of all preprocessors apart from SSL. On Sat, 10 Aug 2019 at 12:43, Grommish [via Itus Networks Owners Forum] <[hidden email]> wrote: You can fork the repo if you want, but realistically, it's bigger than you need unless you plan on trying to build our an image yourself. The only thing that would cause issues with building your own image is that I didn't keep track of the host package requirements. So, you'd have to build out the image and when it errors, add the required package to your system, build out again.. Wash, rinse, repeat until it builds out.
OpenWrt SNAPSHOT, r10391-3d8d528939
|
|
Administrator
|
Check in /etc/rc.local as I know I had put some of the stuff user8446 had suggested here in there. It's why the links jump up and down on boot at the end.
I'm not a massive knowledge base when it comes to Snort, but I have to ask why the preprocessors were suggested to be removed? Performance has yet to taken a hit in this build at all that I can tell, but it might be from Snort having been such an older version? Do me a favor and test with the rules to see if the performance hit is still around? I don't mind losing them, I just wish I had more experience. I've spread the load over both cores and am using afpacket rather than the one Itus used. I know I was testing with ALL the rules from whatever that rule repo was (don't remember offhand) which even they say not to do AND the Snort community rules on both incoming and outgoing traffic (eth0 and br-lan) without issue. It was something like 28000 rules all told, and I still hit my link Max of 200-225Mbps down with under a 1.0 load *shrug* Right now, the system has 400mb free (of the 1gb) RAM after Snort and e2 guardian loads (along with everything else) Oh! Before I forget again. I did add full Python support on it, in case you or someone has need of it.
Running Itus Shield v2 Firmware
|
|
/etc/rc.local currently just has gpio switch stuff to set the orange LED. If you've got additions working from user8446, let me know & I can add to a PR (or re-grab from your repo). Unfortunately I'm not a big snorter either ;) so hopefully you're right about it just being a problem with the older version. I'll give it a whirl - going to try load in some extra rules from the old fw_upgrade script. Let you know how it goes. Btw - no spontaneous reboots btw since last week, and the case is still on :) On Sat, 10 Aug 2019 at 14:52, Grommish [via Itus Networks Owners Forum] <[hidden email]> wrote: Check in /etc/rc.local as I know I had put some of the stuff user8446 had suggested here in there. It's why the links jump up and down on boot at the end.
OpenWrt SNAPSHOT, r10391-3d8d528939
|
|
In reply to this post by Grommish
Hi Grommish
One down - I've created a script for /etc/snort/updaterules.sh that could be cron'd weekly, or run on demand. Sample output via CLI: 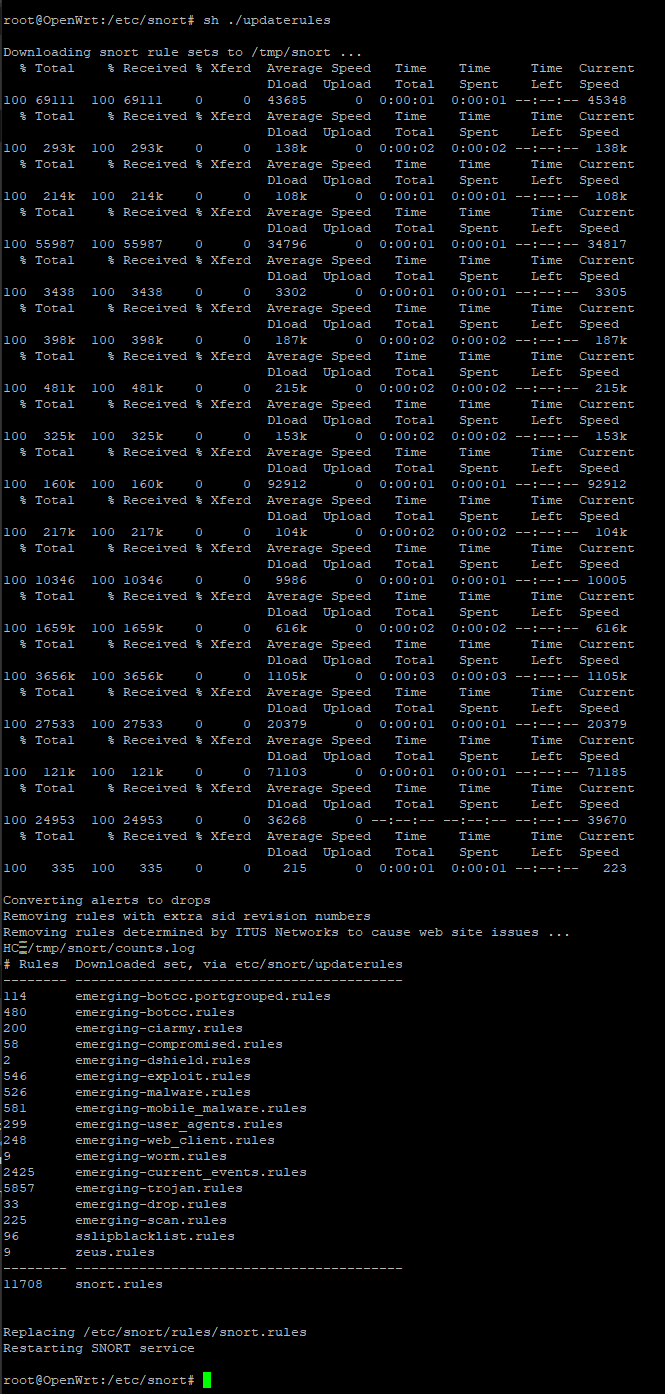
OpenWrt SNAPSHOT, r10391-3d8d528939
|
|
Administrator
|
Fantastic. I know the ET rules are set to ALERT and not DROP. Thoughts on changing that? On Sun, Aug 11, 2019, 1:57 AM Gnomad [via Itus Networks Owners Forum] <[hidden email]> wrote: Hi GrommishOne down - I've created a script for /etc/snort/updaterules.sh that could be cron'd weekly, or run on demand.
Running Itus Shield v2 Firmware
|
|
Done!
I've also just updated the gist to remove ZeuS which appears discontinued, and unpack and include the latest Snort 2.9 community rules from https://www.snort.org/downloads/#rule-downloads ~ 11,700 all up. 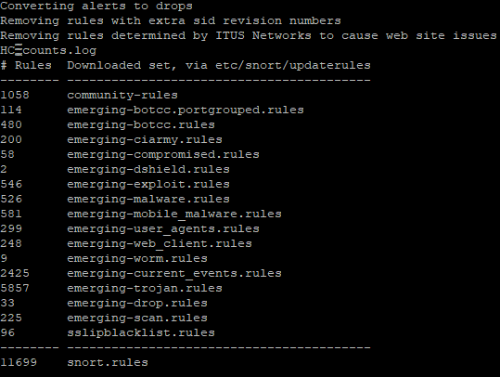
OpenWrt SNAPSHOT, r10391-3d8d528939
|
«
Return to Technical Discussion
|
1 view|%1 views
| Free forum by Nabble | Edit this page |


