Re: Update and decision time.
Posted by Grommish on Jun 20, 2020; 7:54pm
URL: https://itus.accessinnov.com/FIRMWARE-Itus-Shield-v2-tp2014p2064.html
Second, Gnomad, you rock.. I went and created a AWS S3 bucket to hold things (fully expecting to stay within the free tier), but I completely blanked on Github as a resource. That should be totally do-able and it really doesn't matter what the URL is, because you won't ever really see it..
Third, that image you're running contains many, many things. It was a very long journey to figure out why the network did and didn't work sometimes.. Put it this way, that 100MB image file actually has FULL Python3 support :D (among other things) which makes it entirely bloated.. Unless you WANT Python3, which the Shield actually can support..
But.. I've LEARNED things along the way, too. Because the image is RAM resident at boot, AND contains the kernel (in the BIN image, NOT as a vmlinux file!).. it doesn't really get unloaded from RAM, which means my idle when I have the bone-stock image looks like this (Granted, I'm not running ~600MB of RAM towards Snort yet!)
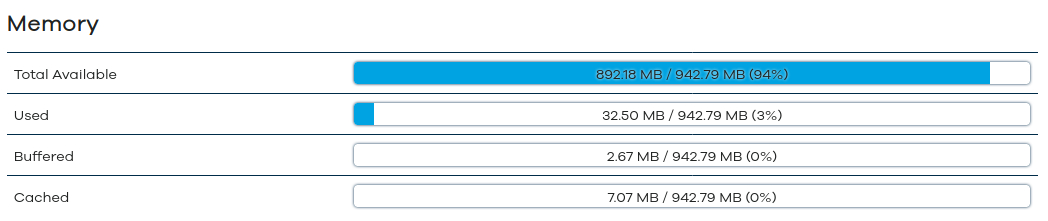
More RAM = More playspace.. Especially if I can figure out a legit upgrade path (and I'm working on it). We will NEVER be able to get away from rebooting the device because of the kernel issue (AFAIK, anyway, I've been wrong before), but we can make it quicker. Right now (again, not counting Snort, which you are running and takes a LOT of resources).. my "boot" time is about 60-70 seconds..
I've never heard of bcp38, but I will look at it (and see if it's an OpenWrt package or not).. How does SQM interact with QOS? Are they the same, different, completely different? Currently, pre-installed on the image is DNSMASQ, which acts like the DNS/DHCP resolver and server. I'm sure there is a way to have DNSMASQ use DoH, but I only looked at it quickly in the beginning. So, DoH is a solution, though it would be available only for Router mode, of course..
Wireguard is available.. OpenVPN is available. Both are accessable thru luCi even. I know OpenVPN will work, because I've tested it. Wireguard will work, but I can't test because my VPN doesn't have publicly available WG info (they make you use their client..) but it IS in there for those that can.
AND.. For those who REALLY don't like CLI..
I'd added a luCi shell page..
URL: https://itus.accessinnov.com/FIRMWARE-Itus-Shield-v2-tp2014p2064.html
First, thanks to all of you for being awesome during the devel time..
Second, Gnomad, you rock.. I went and created a AWS S3 bucket to hold things (fully expecting to stay within the free tier), but I completely blanked on Github as a resource. That should be totally do-able and it really doesn't matter what the URL is, because you won't ever really see it..
Third, that image you're running contains many, many things. It was a very long journey to figure out why the network did and didn't work sometimes.. Put it this way, that 100MB image file actually has FULL Python3 support :D (among other things) which makes it entirely bloated.. Unless you WANT Python3, which the Shield actually can support..
But.. I've LEARNED things along the way, too. Because the image is RAM resident at boot, AND contains the kernel (in the BIN image, NOT as a vmlinux file!).. it doesn't really get unloaded from RAM, which means my idle when I have the bone-stock image looks like this (Granted, I'm not running ~600MB of RAM towards Snort yet!)

More RAM = More playspace.. Especially if I can figure out a legit upgrade path (and I'm working on it). We will NEVER be able to get away from rebooting the device because of the kernel issue (AFAIK, anyway, I've been wrong before), but we can make it quicker. Right now (again, not counting Snort, which you are running and takes a LOT of resources).. my "boot" time is about 60-70 seconds..
[ 58.465366] IPv6: ADDRCONF(NETDEV_CHANGE): eth0: link becomes ready
and the network it up and running..See, this is why I would really like to do the platform, rather than a turnkey (I know, I know). This way, anyone who wants whatever can grab it..
I've never heard of bcp38, but I will look at it (and see if it's an OpenWrt package or not).. How does SQM interact with QOS? Are they the same, different, completely different? Currently, pre-installed on the image is DNSMASQ, which acts like the DNS/DHCP resolver and server. I'm sure there is a way to have DNSMASQ use DoH, but I only looked at it quickly in the beginning. So, DoH is a solution, though it would be available only for Router mode, of course..
Wireguard is available.. OpenVPN is available. Both are accessable thru luCi even. I know OpenVPN will work, because I've tested it. Wireguard will work, but I can't test because my VPN doesn't have publicly available WG info (they make you use their client..) but it IS in there for those that can.
AND.. For those who REALLY don't like CLI..
I'd added a luCi shell page..

Running Itus Shield v2 Firmware
| Free forum by Nabble | Edit this page |