Re: [FIRMWARE] Itus Networks Shield Firmware Upgrade *WIP*
Posted by Grommish on Jun 23, 2019; 6:22am
URL: https://itus.accessinnov.com/FIRMWARE-Itus-Networks-Shield-Firmware-Upgrade-WIP-tp1726p1771.html
Thanks! So, you do the Lua *peer* haha.
One of the advantages to being able to actually work on-device now for a lot of things is that I can rob the bones of the Itus images in place. I can just mount the overlay for the other images and walk through things.
I'm working on the Snort Lua stuff at the moment. I pulled the stuff, although interesting enough, it was either being setup for Suricata, or borrowed from the Suricata package.. I looked into getting Suricata in the build, but finally put it aside for now. Suricata doesn't support cross-compiling for mips, meh.. If they ever get it working, I can add it easy enough. I already have the package hooks for it.
The rule files for the Itus image has Snort dropping rather than alerting like the public rules do. Do we want to continue with that? I'm down to learn new things like Lua, OpenWrt, Snort, etc, but if I have to sit down and learn functional sed and regex, it's going to slow my down considerably.
I'm pretty sure you're the one that is tagging my repo for this, so if you feel froggy, let me know and I'll do the pull request :D if i had been smart, I'd have set up the git repo from the start, but eh. the important bits are there. It's been a long time since I used git (as you can tell from my other repos), so I'm still feeling my way around it again..
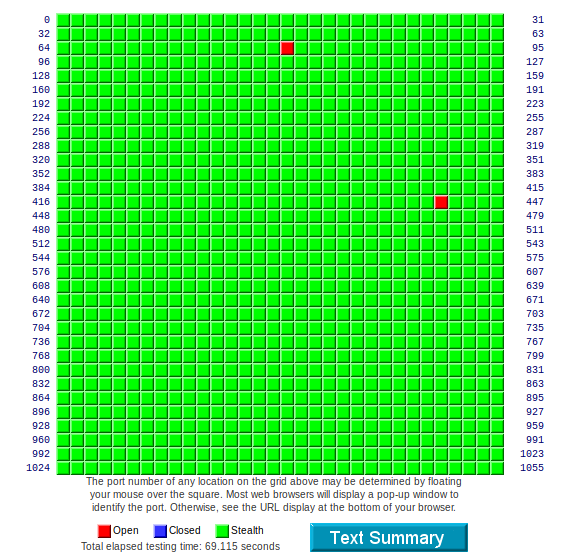
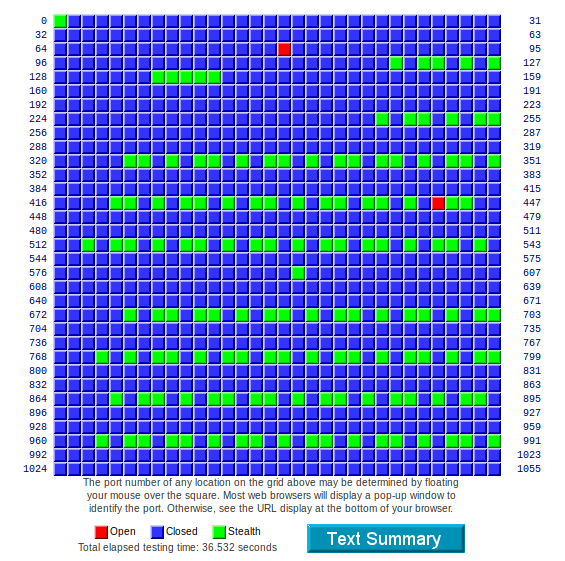
In any case, I'll work through it. I figure I'll work Snort first, since it is the main reason for the device. Then, maybe move on to e2guardian, and then go from there. I know the FIREWALL needs to be tweaked something fierce. I DMZ'd the shield and scanned it, and so many closed-but-not-stealthed ports.. Can't let this stand. And yes, the 80:443 open ports are not the Shield, which shouldn't be exposed anyway by default.
Standard Scan
DMZ'd Shield
URL: https://itus.accessinnov.com/FIRMWARE-Itus-Networks-Shield-Firmware-Upgrade-WIP-tp1726p1771.html
Thanks! So, you do the Lua *peer* haha.
One of the advantages to being able to actually work on-device now for a lot of things is that I can rob the bones of the Itus images in place. I can just mount the overlay for the other images and walk through things.
I'm working on the Snort Lua stuff at the moment. I pulled the stuff, although interesting enough, it was either being setup for Suricata, or borrowed from the Suricata package.. I looked into getting Suricata in the build, but finally put it aside for now. Suricata doesn't support cross-compiling for mips, meh.. If they ever get it working, I can add it easy enough. I already have the package hooks for it.
The rule files for the Itus image has Snort dropping rather than alerting like the public rules do. Do we want to continue with that? I'm down to learn new things like Lua, OpenWrt, Snort, etc, but if I have to sit down and learn functional sed and regex, it's going to slow my down considerably.
I'm pretty sure you're the one that is tagging my repo for this, so if you feel froggy, let me know and I'll do the pull request :D if i had been smart, I'd have set up the git repo from the start, but eh. the important bits are there. It's been a long time since I used git (as you can tell from my other repos), so I'm still feeling my way around it again..
In any case, I'll work through it. I figure I'll work Snort first, since it is the main reason for the device. Then, maybe move on to e2guardian, and then go from there. I know the FIREWALL needs to be tweaked something fierce. I DMZ'd the shield and scanned it, and so many closed-but-not-stealthed ports.. Can't let this stand. And yes, the 80:443 open ports are not the Shield, which shouldn't be exposed anyway by default.
Standard Scan

DMZ'd Shield

Running Itus Shield v2 Firmware
| Free forum by Nabble | Edit this page |