Internet speed slower in bridge mode
12345

12345
|
Thanks, Roadrunnere42 it looks like I got it here screen shot do I have to reboot to see if my speed goes up ?
Thanks again 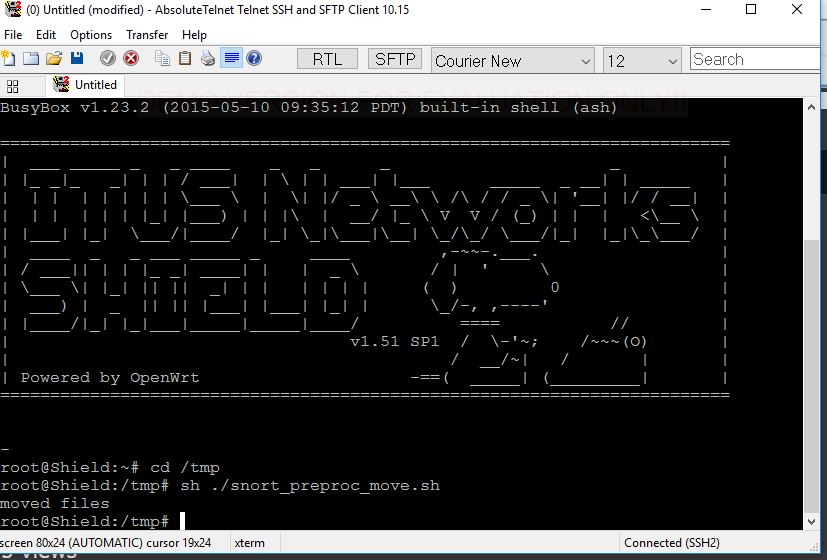
|
Re: Internet speed slower in bridge mode
|
breda
I'm not sure but it never hurts to reboot, I personal don't get too hooked up on the speeds as a lot of the isp server are optimized to give max download speeds when speed test are run, remember you only get what the server your downloading or streaming from can give. I test by downloading a operating OS of say about 1gb usually a linux one, i time from when i started the download till its completed, then do the same but without the Shield. Now compare the time and i bet these not a great difference I'm on Virgin media and they just keep upgrading my speeds free of charge first from 2mb then 20mb now 50mb and in reel terms I have not notice any difference in speed. just my thoughts. Roadrunnere42 |
|
Hi, Roadrunnere42 thanks for the help I did reboot but still only getting 47.72Mb/s when I do download test with the shield in line and I get 105.59Mb/s without the Shield I used the same server
Here is the speed with shield http://www.speedtest.net/my-result/5595516959 Here is the speed without shield http://www.speedtest.net/my-result/5595519762 also here is my system log system_log_8-30-16.txt |
|
In reply to this post by Roadrunnere42
also looking at the logs every time I do speed test I see these errors
Thanks Wed Sep 7 17:57:02 2016 daemon.notice snort[17024]: S5: Session exceeded configured max bytes to queue 3137628 using 3137790 bytes (server queue). 66.234.209.81 53916 --> 204.11.104.30 8080 (0) : LWstate 0x9 LWFlags 0x6007 Wed Sep 7 17:57:08 2016 daemon.notice snort[17024]: S5: Pruned 5 sessions from cache for memcap. 111 scbs remain. memcap: 8421442/8388608 Wed Sep 7 17:57:08 2016 daemon.notice snort[17024]: S5: Pruned 5 sessions from cache for memcap. 106 scbs remain. memcap: 8423035/8388608 Wed Sep 7 17:57:08 2016 daemon.notice snort[17024]: S5: Pruned 5 sessions from cache for memcap. 101 scbs remain. memcap: 8424628/8388608 Wed Sep 7 17:57:08 2016 daemon.notice snort[17024]: S5: Pruned 5 sessions from cache for memcap. 96 scbs remain. memcap: 8426221/8388608 Wed Sep 7 17:57:08 2016 daemon.notice snort[17024]: S5: Pruned 5 sessions from cache for memcap. 91 scbs remain. memcap: 8427814/8388608 Wed Sep 7 17:57:08 2016 daemon.notice snort[17024]: S5: Pruned 5 sessions from cache for memcap. 86 scbs remain. memcap: 8427718/8388608 Wed Sep 7 17:57:08 2016 daemon.notice snort[17024]: S5: Pruned 5 sessions from cache for memcap. 81 scbs remain. memcap: 8429311/8388608 Wed Sep 7 17:57:08 2016 daemon.notice snort[17024]: S5: Pruned 5 sessions from cache for memcap. 76 scbs remain. memcap: 8430705/8388608 Wed Sep 7 17:57:08 2016 daemon.notice snort[17024]: S5: Pruned 5 sessions from cache for memcap. 71 scbs remain. memcap: 8428913/8388608 Wed Sep 7 17:57:08 2016 daemon.notice snort[17024]: S5: Pruned 5 sessions from cache for memcap. 66 scbs remain. memcap: 8430311/8388608 Wed Sep 7 17:57:08 2016 daemon.notice snort[17024]: S5: Pruned 5 sessions from cache for memcap. 61 scbs remain. memcap: 8430497/8388608 Wed Sep 7 17:57:08 2016 daemon.notice snort[17024]: S5: Pruned 5 sessions from cache for memcap. 56 scbs remain. memcap: 8432090/8388608 Wed Sep 7 17:57:08 2016 daemon.notice snort[17024]: S5: Pruned 5 sessions from cache for memcap. 51 scbs remain. memcap: 8432409/8388608 Wed Sep 7 17:57:08 2016 daemon.notice snort[17024]: S5: Pruned 5 sessions from cache for memcap. 46 scbs remain. memcap: 8434002/8388608 Wed Sep 7 17:57:08 2016 daemon.notice snort[17024]: S5: Pruned 5 sessions from cache for memcap. 41 scbs remain. memcap: 8433577/8388608 Wed Sep 7 17:57:08 2016 daemon.notice snort[17024]: S5: Pruned 5 sessions from cache for memcap. 36 scbs remain. memcap: 8432732/8388608 Wed Sep 7 17:57:08 2016 daemon.notice snort[17024]: S5: Pruned 5 sessions from cache for memcap. 31 scbs remain. memcap: 8434325/8388608 Wed Sep 7 17:57:08 2016 daemon.notice snort[17024]: S5: Pruned 5 sessions from cache for memcap. 26 scbs remain. memcap: 8435918/8388608 Wed Sep 7 17:57:08 2016 daemon.notice snort[17024]: S5: Pruned 5 sessions from cache for memcap. 21 scbs remain. memcap: 7977179/8388608 Wed Sep 7 17:57:08 2016 daemon.notice snort[17024]: S5: Pruned 1 sessions from cache for memcap. 26 scbs remain. memcap: 8388312/8388608 Wed Sep 7 17:57:08 2016 daemon.notice snort[17024]: S5: Pruned 4 sessions from cache for memcap. 24 scbs remain. memcap: 8388198/8388608 Wed Sep 7 17:57:08 2016 daemon.notice snort[17024]: S5: Pruned 2 sessions from cache for memcap. 22 scbs remain. memcap: 8388334/8388608 Wed Sep 7 17:57:08 2016 daemon.notice snort[17024]: S5: Pruned 5 sessions from cache for memcap. 17 scbs remain. memcap: 8389714/8388608 Wed Sep 7 17:57:08 2016 daemon.notice snort[17024]: S5: Pruned 5 sessions from cache for memcap. 12 scbs remain. memcap: 8389261/8388608 Wed Sep 7 17:57:08 2016 daemon.notice snort[17024]: S5: Pruned 5 sessions from cache for memcap. 7 scbs remain. memcap: 8389562/8388608 Wed Sep 7 17:57:09 2016 daemon.notice snort[17024]: S5: Pruned session from cache that was using 3306519 bytes (memcap/check). 66.234.209.81 53916 --> 204.11.104.30 8080 (0) : LWstate 0x9 LWFlags 0x6007 Wed Sep 7 17:57:09 2016 daemon.notice snort[17024]: S5: Pruned 5 sessions from cache for memcap. 5 scbs remain. memcap: 5084636/8388608 Wed Sep 7 17:57:10 2016 daemon.notice snort[17024]: S5: Session exceeded configured max bytes to queue 3137628 using 3138227 bytes (server queue). 66.234.209.81 53917 --> 204.11.104.30 8080 (0) : LWstate 0x9 LWFlags 0x6007 |
|
In reply to this post by Roadrunnere42
Hi, @Roadrunnere42 @user8446 just checking to see if you have any recommendation on how I can get faster WAN Speed on my shield looking at the logs I get a lot of these errors anytime I do speed test
Thaks Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 215 scbs remain. memcap: 8393593/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 210 scbs remain. memcap: 8394618/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 205 scbs remain. memcap: 8394477/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 200 scbs remain. memcap: 8395105/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 195 scbs remain. memcap: 8395483/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 190 scbs remain. memcap: 8394671/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 185 scbs remain. memcap: 8393859/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 180 scbs remain. memcap: 8394774/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 175 scbs remain. memcap: 8395509/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 170 scbs remain. memcap: 8395706/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 165 scbs remain. memcap: 8394154/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 160 scbs remain. memcap: 8395747/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 155 scbs remain. memcap: 8397340/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 150 scbs remain. memcap: 8398933/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 145 scbs remain. memcap: 8400526/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 140 scbs remain. memcap: 8400637/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 135 scbs remain. memcap: 8401720/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 130 scbs remain. memcap: 8400734/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 125 scbs remain. memcap: 8401428/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 120 scbs remain. memcap: 8403021/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 115 scbs remain. memcap: 8400569/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 110 scbs remain. memcap: 8399723/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 105 scbs remain. memcap: 8400988/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 100 scbs remain. memcap: 8402069/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 95 scbs remain. memcap: 8400353/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 90 scbs remain. memcap: 8400559/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 85 scbs remain. memcap: 8401953/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 80 scbs remain. memcap: 8402044/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 75 scbs remain. memcap: 8400278/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 70 scbs remain. memcap: 8399845/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 65 scbs remain. memcap: 8396896/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 4 sessions from cache for memcap. 61 scbs remain. memcap: 8386053/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 56 scbs remain. memcap: 8389239/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 3 sessions from cache for memcap. 53 scbs remain. memcap: 8388557/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 48 scbs remain. memcap: 8389526/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 4 sessions from cache for memcap. 44 scbs remain. memcap: 8388273/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 39 scbs remain. memcap: 8387544/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 4 sessions from cache for memcap. 41 scbs remain. memcap: 8388596/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 3 sessions from cache for memcap. 38 scbs remain. memcap: 8388537/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 3 sessions from cache for memcap. 36 scbs remain. memcap: 8387634/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 31 scbs remain. memcap: 8371166/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 1 sessions from cache for memcap. 30 scbs remain. memcap: 8388150/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 27 scbs remain. memcap: 8379728/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 1 sessions from cache for memcap. 26 scbs remain. memcap: 8383954/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 1 sessions from cache for memcap. 25 scbs remain. memcap: 8388194/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 20 scbs remain. memcap: 8388736/8388608 Sat Sep 17 11:52:29 2016 daemon.notice snort[21293]: S5: Pruned 5 sessions from cache for memcap. 15 scbs remain. memcap: 7046967/8388608 Sat Sep 17 11:52:32 2016 daemon.notice snort[21293]: S5: Session exceeded configured max bytes to queue 3137628 using 3138273 bytes (server queue). 66.234.209.81 65048 --> 216.38.158.170 8080 (0) : LWstate 0x9 LWFlags 0x6007 |
|
Administrator
|
Hi Breda,
You are hitting the default 8mb memcap and your 3mb queue. Lets add a mb to both in your snort config: ...snip... preprocessor stream5_global: track_tcp yes, \ track_udp yes, \ track_icmp yes, \ max_tcp 10000, \ max_udp 10000, \ memcap 9388608, \ max_active_responses 2, \ min_response_seconds 5, \ prune_log_max 4194304 preprocessor stream5_tcp: policy windows, detect_anomalies, require_3whs 180, \ overlap_limit 10, small_segments 3 bytes 150, timeout 180, \ max_queued_bytes 4194304, \ ports client 21 22 23 25 42 53 70 79 109 110 111 113 119 135 136 137 139 143 \ 161 445 513 514 587 593 691 1433 1521 1741 2100 3306 6070 6665 6666 6667 6668 6669 \ 7000 8181 32770 32771 32772 32773 32774 32775 32776 32777 32778 32779, \ ports both 36 80 81 82 83 84 85 86 87 88 89 90 110 311 383 443 465 563 555 591 593 631 636 801 808 818 901 972 989 992 993 994 995 1158 1220 1414 1533 1741 1830 1942 2231 2301 2381 2809 2980 3029 3037 3057 3128 3443 3702 4000 4343 4848 5000 5117 5250 5600 6080 6173 6988 7907 7000 7001 7071 7144 7145 7510 7802 7770 7777 7778 7779 \ 7801 7900 7901 7902 7903 7904 7905 7906 7908 7909 7910 7911 7912 7913 7914 7915 7916 \ 7917 7918 7919 7920 8000 8008 8014 8028 8080 8081 8082 8085 8088 8090 8118 8123 8180 8181 8222 8243 8280 8300 8333 8344 8500 8509 8800 8888 8899 8983 9000 9060 9080 9090 9091 9111 9290 9443 9999 10000 11371 12601 13014 15489 29991 33300 34412 34443 34444 41080 44449 50000 50002 51423 53331 55252 55555 56712 preprocessor stream5_udp: timeout 180 ...snip...
Running the latest OpenWrt stable release
|
|
HI, user8446 I cut and pasted your update in Snort Configuration but still getting these errors shen I run speed test I will attach my Snort Configuration and the speed it still the same thanks for the help Snort_Configuration.txt Sat Sep 24 13:10:31 2016 daemon.notice snort[26733]: S5: Session exceeded configured max segs to queue 2621 using 2621 segs (server queue). 66.234.209.81 64927 --> 204.11.104.30 8080 (0) : LWstate 0xf LWFlags 0x406007 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 5 sessions from cache for memcap. 172 scbs remain. memcap: 9402518/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 5 sessions from cache for memcap. 167 scbs remain. memcap: 9400444/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 5 sessions from cache for memcap. 162 scbs remain. memcap: 9400266/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 5 sessions from cache for memcap. 157 scbs remain. memcap: 9397219/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 5 sessions from cache for memcap. 152 scbs remain. memcap: 9396724/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 5 sessions from cache for memcap. 147 scbs remain. memcap: 9392927/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 5 sessions from cache for memcap. 142 scbs remain. memcap: 9391825/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 5 sessions from cache for memcap. 138 scbs remain. memcap: 9390232/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 5 sessions from cache for memcap. 133 scbs remain. memcap: 9391825/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 5 sessions from cache for memcap. 128 scbs remain. memcap: 9389134/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 5 sessions from cache for memcap. 123 scbs remain. memcap: 9390563/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 5 sessions from cache for memcap. 118 scbs remain. memcap: 9388970/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 5 sessions from cache for memcap. 113 scbs remain. memcap: 9390384/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 2 sessions from cache for memcap. 111 scbs remain. memcap: 9387414/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 5 sessions from cache for memcap. 106 scbs remain. memcap: 9389007/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 5 sessions from cache for memcap. 101 scbs remain. memcap: 9388812/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 2 sessions from cache for memcap. 99 scbs remain. memcap: 9388427/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 5 sessions from cache for memcap. 94 scbs remain. memcap: 9387881/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 1 sessions from cache for memcap. 93 scbs remain. memcap: 9387881/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 5 sessions from cache for memcap. 88 scbs remain. memcap: 9389275/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 5 sessions from cache for memcap. 83 scbs remain. memcap: 9390689/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 5 sessions from cache for memcap. 78 scbs remain. memcap: 9389171/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 4 sessions from cache for memcap. 74 scbs remain. memcap: 9388079/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 2 sessions from cache for memcap. 72 scbs remain. memcap: 9388604/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 3 sessions from cache for memcap. 69 scbs remain. memcap: 9387757/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 1 sessions from cache for memcap. 68 scbs remain. memcap: 9387757/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 1 sessions from cache for memcap. 67 scbs remain. memcap: 9387757/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 1 sessions from cache for memcap. 66 scbs remain. memcap: 9387757/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 5 sessions from cache for memcap. 61 scbs remain. memcap: 9389155/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 5 sessions from cache for memcap. 56 scbs remain. memcap: 9390534/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 5 sessions from cache for memcap. 51 scbs remain. memcap: 9389265/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 3 sessions from cache for memcap. 48 scbs remain. memcap: 9388401/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 5 sessions from cache for memcap. 43 scbs remain. memcap: 9389238/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 5 sessions from cache for memcap. 38 scbs remain. memcap: 9389745/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 5 sessions from cache for memcap. 34 scbs remain. memcap: 9391142/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 5 sessions from cache for memcap. 29 scbs remain. memcap: 9389168/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 2 sessions from cache for memcap. 27 scbs remain. memcap: 9387818/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 3 sessions from cache for memcap. 24 scbs remain. memcap: 9388510/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 3 sessions from cache for memcap. 21 scbs remain. memcap: 9388510/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 1 sessions from cache for memcap. 20 scbs remain. memcap: 9388510/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 4 sessions from cache for memcap. 16 scbs remain. memcap: 9388514/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 3 sessions from cache for memcap. 13 scbs remain. memcap: 9388600/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 5 sessions from cache for memcap. 8 scbs remain. memcap: 9389352/9388608 Sat Sep 24 13:10:32 2016 daemon.notice snort[26733]: S5: Pruned 1 sessions from cache for memcap. 7 scbs remain. memcap: 5379283/9388608 |
|
Administrator
|
Still hitting the memcap... raise it to 11388608
Running the latest OpenWrt stable release
|
|
Thanks user8446 I will increase memcap is my Snort_Configuration file configured correctly?
|
|
In reply to this post by user8446
Hi, user8446 thanks for the help not getting the memcap error but still can't seem to get over 56 Mbs here are some errors in the logs Fri Sep 30 11:06:48 2016 daemon.err uhttpd[4624]: cut: standard output: Broken pipe Fri Sep 30 11:07:00 2016 daemon.notice snort[30889]: S5: Session exceeded configured max segs to queue 2621 using 2621 segs (server queue). 66.234.209.81 58807 --> 204.11.104.30 8080 (0) : LWstate 0x9 LWFlags 0x6007 |
|
Administrator
|
In your Snort config, add this line right below your max_queued_bytes :
max_queued_segs 3621, \ Click "save & apply" and it'll restart Snort
Running the latest OpenWrt stable release
|
|
Hi, user8446 thanks for the help I added the line and Save & Apply and restated the shield still will not go over 50 Mbs
preprocessor stream5_tcp: policy windows, detect_anomalies, require_3whs 180, \ overlap_limit 10, small_segments 3 bytes 150, timeout 180, \ max_queued_bytes 4194304, \ max_queued_segs 3621, \ Mon Oct 10 17:21:42 2016 daemon.notice snort[5079]: Writing PID "5079" to file "/var/snort//snort_eth0:eth2.pid" Mon Oct 10 17:21:42 2016 daemon.notice snort[5079]: Mon Oct 10 17:21:42 2016 daemon.notice snort[5079]: --== Initialization Complete ==-- Mon Oct 10 17:21:42 2016 daemon.notice snort[5079]: Mon Oct 10 17:21:42 2016 daemon.notice snort[5079]: ,,_ -*> Snort! <*- Mon Oct 10 17:21:42 2016 daemon.notice snort[5079]: o" )~ Version 2.9.7.2 GRE (Build 177) Mon Oct 10 17:21:42 2016 daemon.notice snort[5079]: '''' By Martin Roesch & The Snort Team: http://www.snort.org/contact#team Mon Oct 10 17:21:42 2016 daemon.notice snort[5079]: Copyright (C) 2014 Cisco and/or its affiliates. All rights reserved. Mon Oct 10 17:21:42 2016 daemon.notice snort[5079]: Copyright (C) 1998-2013 Sourcefire, Inc., et al. Mon Oct 10 17:21:42 2016 daemon.notice snort[5079]: Using libpcap version 1.5.3 Mon Oct 10 17:21:42 2016 daemon.notice snort[5079]: Using PCRE version: 8.36 2014-09-26 Mon Oct 10 17:21:42 2016 daemon.notice snort[5079]: Using ZLIB version: 1.2.8 Mon Oct 10 17:21:42 2016 daemon.notice snort[5079]: Mon Oct 10 17:21:42 2016 daemon.notice snort[5079]: Rules Engine: SF_SNORT_DETECTION_ENGINE Version 2.4 <Build 1> Mon Oct 10 17:21:42 2016 daemon.notice snort[5079]: Preprocessor Object: SF_DCERPC2 Version 1.0 <Build 3> Mon Oct 10 17:21:42 2016 daemon.notice snort[5079]: Preprocessor Object: SF_SSH Version 1.1 <Build 3> Mon Oct 10 17:21:42 2016 daemon.notice snort[5079]: Preprocessor Object: SF_DNS Version 1.1 <Build 4> Mon Oct 10 17:21:42 2016 daemon.notice snort[5079]: Preprocessor Object: SF_FTPTELNET Version 1.2 <Build 13> Mon Oct 10 17:21:42 2016 daemon.notice snort[5079]: Preprocessor Object: SF_SSLPP Version 1.1 <Build 4> Mon Oct 10 17:21:42 2016 daemon.notice snort[5079]: Commencing packet processing (pid=5079) Mon Oct 10 17:21:42 2016 daemon.notice snort[5079]: Decoding Ethernet Mon Oct 10 17:21:47 2016 authpriv.info dropbear[3229]: Early exit: Terminated by signal Mon Oct 10 17:21:47 2016 authpriv.info dropbear[5333]: Not backgrounding Mon Oct 10 17:21:47 2016 authpriv.info dropbear[5334]: Not backgrounding Mon Oct 10 17:21:47 2016 authpriv.warn dropbear[5336]: Failed listening on '22': Error listening: Address already in use Mon Oct 10 17:21:47 2016 authpriv.info dropbear[5336]: Early exit: No listening ports available. Mon Oct 10 17:21:47 2016 authpriv.warn dropbear[5335]: Failed listening on '22': Error listening: Address already in use Mon Oct 10 17:21:47 2016 authpriv.info dropbear[5335]: Early exit: No listening ports available. Mon Oct 10 17:23:00 2016 daemon.emerg procd: 42652 01317.849 119465.0 91.4 62989177.1 32455.4 0 Mon Oct 10 17:23:00 2016 user.notice root: Successful NTP clock adjust (0.us.pool.ntp.org). Mon Oct 10 17:23:01 2016 daemon.info procd: - init complete - Mon Oct 10 17:25:21 2016 daemon.notice snort[5079]: S5: Session exceeded configured max bytes to queue 4194304 using 4195238 bytes (server queue). 66.234.209.81 60689 --> 216.38.158.170 8080 (0) : LWstate 0x9 LWFlags 0x406007 |
|
Administrator
|
Go to system>startup>network (restart). Check your kernal log and make sure you see:
eth0: 1000 Mbps Full duplex, port 0 eth2: 1000 Mbps Full duplex, port 2 not 100Mbps.
Running the latest OpenWrt stable release
|
|
This post was updated on .
Hi, user8446 I did restart but now lost all internet via the shield
here is the system log Tue Oct 18 18:46:18 2016 daemon.notice vnstatd[4210]: Traffic rate for "br-lan" higher than set maximum 100 Mbit (60->825, r3949 t4075), syncing. here is the Kernel Log [696282.622081] br-lan: port 1(eth1) entered disabled state [696282.623561] device eth1 left promiscuous mode [696282.623580] br-lan: port 1(eth1) entered disabled state [696282.643507] eth1: Link down [696282.644275] IPv6: ADDRCONF(NETDEV_UP): eth1: link is not ready [696282.734497] eth0: Link down [696282.774972] eth2: Link down [696284.070309] eth1: 1000 Mbps Full duplex, port 1 [696284.071161] device eth1 entered promiscuous mode [696284.072182] br-lan: port 1(eth1) entered forwarding state [696284.072207] br-lan: port 1(eth1) entered forwarding state [696284.109942] eth0: 1000 Mbps Full duplex, port 0 [696284.131460] eth2: 1000 Mbps Full duplex, port 2 [696285.124034] eth2: Link down [696286.064188] br-lan: port 1(eth1) entered forwarding state |
|
In reply to this post by user8446
Hi, user8446 thank you for the help got the shield back up but sill only getting 50 Mbps and without the shield, I get 105 Mbps
Here is the Kernel Log [ 362.823428] eth0: 1000 Mbps Full duplex, port 0 [ 362.845134] eth2: 1000 Mbps Full duplex, port 2 [ 363.843962] eth2: Link down [ 364.784121] br-lan: port 1(eth1) entered forwarding state [ 669.783987] eth1: Link down [ 669.784049] br-lan: port 1(eth1) entered disabled state [ 670.778687] IPv6: ADDRCONF(NETDEV_UP): eth2: link is not ready [ 699.794156] eth1: 1000 Mbps Full duplex, port 1 [ 699.794190] br-lan: port 1(eth1) entered forwarding state [ 699.794220] br-lan: port 1(eth1) entered forwarding state [ 699.834168] eth2: 1000 Mbps Full duplex, port 2 [ 699.834210] IPv6: ADDRCONF(NETDEV_CHANGE): eth2: link becomes ready [ 701.794102] br-lan: port 1(eth1) entered forwarding state [ 773.813953] eth1: Link down [ 773.814279] br-lan: port 1(eth1) entered disabled state [ 784.824197] eth1: 1000 Mbps Full duplex, port 1 [ 784.824230] br-lan: port 1(eth1) entered forwarding state [ 784.824259] br-lan: port 1(eth1) entered forwarding state [ 786.824099] br-lan: port 1(eth1) entered forwarding state here is the system log port 1(eth1) entered disabled state Sat Oct 22 15:48:54 2016 daemon.notice netifd: Bridge 'br-lan' link is down Sat Oct 22 15:48:54 2016 daemon.notice netifd: Interface 'lan' has link connectivity loss Sat Oct 22 15:48:54 2016 daemon.notice netifd: Interface 'blockdomain' has link connectivity loss Sat Oct 22 15:49:04 2016 daemon.notice netifd: Network device 'eth1' link is up Sat Oct 22 15:49:04 2016 daemon.notice netifd: Bridge 'br-lan' link is up Sat Oct 22 15:49:04 2016 daemon.notice netifd: Interface 'lan' has link connectivity Sat Oct 22 15:49:04 2016 daemon.notice netifd: Interface 'blockdomain' has link connectivity Sat Oct 22 15:49:04 2016 kern.notice kernel: [ 784.824197] eth1: 1000 Mbps Full duplex, port 1 Sat Oct 22 15:49:04 2016 kern.info kernel: [ 784.824230] br-lan: port 1(eth1) entered forwarding state Sat Oct 22 15:49:04 2016 kern.info kernel: [ 784.824259] br-lan: port 1(eth1) entered forwarding state Sat Oct 22 15:49:06 2016 kern.info kernel: [ 786.824099] br-lan: port 1(eth1) entered forwarding state Here is my Local Startup # Put your custom commands here that should be executed once # the system init finished. By default this file does nothing. sleep 5 ethtool -K eth0 gro off ethtool -K eth0 gso off ethtool -K eth0 lro off ifconfig eth0 up sleep 1 ethtool -s eth0 autoneg off sleep 1 ethtool -s eth0 autoneg on sleep 1 ethtool -K eth1 gro off ethtool -K eth1 gso off ethtool -K eth1 lro off ifconfig eth1 up sleep 1 ethtool -s eth1 autoneg off sleep 1 ethtool -s eth1 autoneg on sleep 1 ethtool -K eth2 gro off ethtool -K eth2 gso off ethtool -K eth2 lro off ifconfig eth2 up sleep 1 ethtool -s eth2 autoneg off sleep 1 ethtool -s eth2 autoneg on sleep 1 chown -R nobody:nogroup /tmp/* sleep 1 /etc/itus/detect_mode.sh # Detects the shield mode sleep 1 /etc/init.d/vnstat enable # Vnstat Enable Autostart /etc/init.d/vnstat start # Vnstat Start /etc/init.d/ipsec stop # strongSwan Stop /etc/init.d/ipsec disable # strongSwan Disable Autostart sleep 2 /etc/init.d/dnsmasq restart touch /var/run/ddns/lucihelper.err sh /etc/itus-setup.sh &>/dev/null sleep 30 /etc/init.d/dropbear restart sleep 10 /usr/sbin/ntpclient -s -p 123 -h 0.us.pool.ntp.org || /etc/init.d/ntpclient restart exit 0 Here is the screen shot of the system Startup 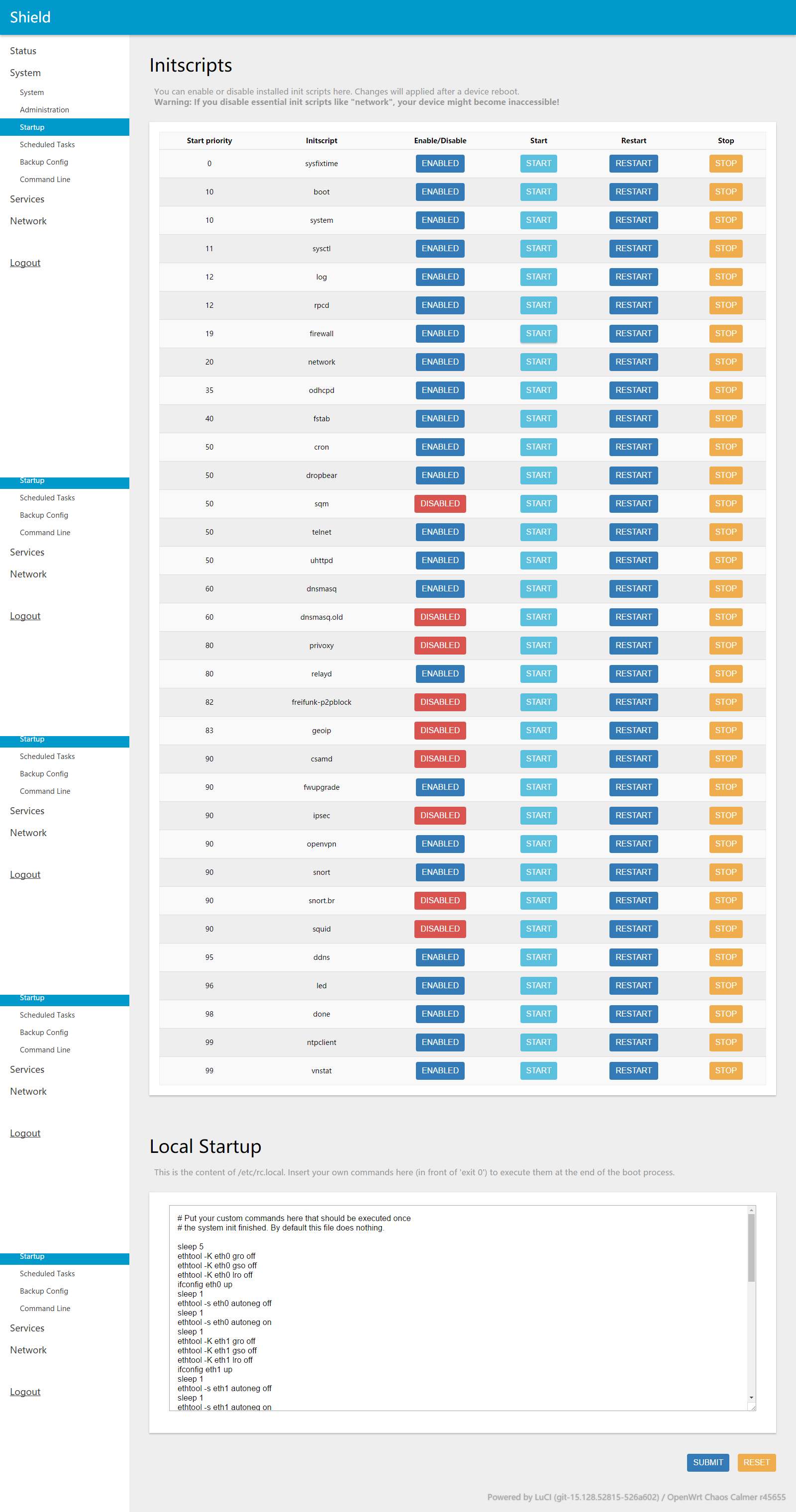 |
|
In reply to this post by user8446
Hi, user8446 just powered on different shield I got off eBay and I still can only get about 54 Mbps down I will attched screen shots and system log also how can I confirm that I'm running the latest firmware and updates from http://itus.accessinnov.com/
system log new_Shield.txt 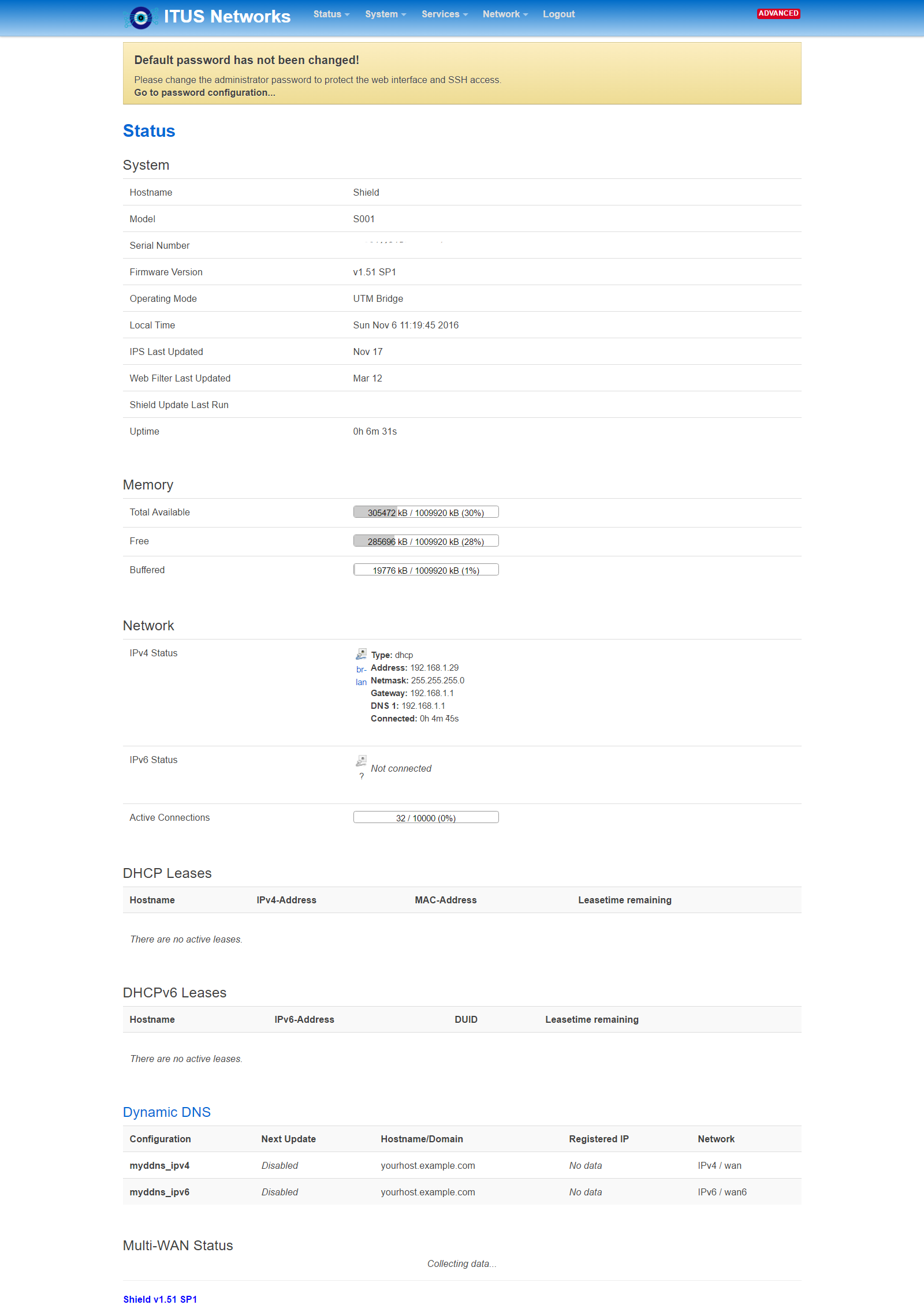 Thanks |
|
Administrator
|
Hi Breda,
use this updated startup: sleep 5 ethtool -K eth0 gro off ethtool -K eth0 gso off ethtool -K eth0 tx-nocache-copy off ifconfig eth0 up sleep 1 ethtool -s eth0 autoneg off sleep 1 ethtool -s eth0 autoneg on sleep 1 ethtool -K eth1 gro off ethtool -K eth1 gso off ethtool -K eth1 tx-nocache-copy off ifconfig eth1 up sleep 1 ethtool -s eth1 autoneg off sleep 1 ethtool -s eth1 autoneg on sleep 1 ethtool -K eth2 gro off ethtool -K eth2 gso off ethtool -K eth2 tx-nocache-copy off ifconfig eth2 up sleep 1 ethtool -s eth2 autoneg off sleep 1 ethtool -s eth2 autoneg on sleep 1 chown -R nobody:nogroup /tmp/* sleep 1 #/etc/init.d/vnstat enable # Vnstat Enable Autostart #/etc/init.d/vnstat start # Vnstat Start /etc/init.d/ipsec stop # strongSwan Stop /etc/init.d/ipsec disable # strongSwan Disable Autostart sleep 2 /etc/init.d/dnsmasq restart touch /var/run/ddns/lucihelper.err sh /etc/itus-setup.sh &>/dev/null sleep 30 /etc/init.d/dropbear restart sleep 30 /usr/sbin/ntpclient -s -p 123 -h 0.us.pool.ntp.org || /etc/init.d/ntpclient restart exit 0 ------------------------ I also see DDNS is spamming your log so go to services>dynamic DNS and delete the two example entries. Now, we can start by using this updated snort config: ipvar HOME_NET any ipvar EXTERNAL_NET any ipvar DNS_SERVERS $HOME_NET ipvar SMTP_SERVERS $HOME_NET ipvar HTTP_SERVERS $HOME_NET ipvar SQL_SERVERS [192.168.0.0/16,10.0.0.0/8,172.16.0.0/12] ipvar TELNET_SERVERS $HOME_NET ipvar SSH_SERVERS $HOME_NET ipvar FTP_SERVERS $HOME_NET ipvar SIP_SERVERS $HOME_NET portvar HTTP_PORTS [36,80,81,82,83,84,85,86,87,88,89,90,311,383,555,591,593,631,801,808,818,901,972,1158,1220,1414,1533,1741,1830,1942,2231,2301,2381,2809,2980,3029,3037,3057,3128,3443,3702,4000,4343,4848,5000,5117,5250,5600,6080,6173,6988,7000,7001,7071,7144,7145,7510,7770,7777,7778,7779,8000,8008,8014,8028,8080,8081,8082,8085,8088,8090,8118,8123,8180,8181,8222,8243,8280,8300,8333,8344,8500,8509,8800,8888,8899,8983,9000,9060,9080,9090,9091,9111,9290,9443,9999,10000,11371,12601,13014,15489,29991,33300,34412,34443,34444,41080,44449,50000,50002,51423,53331,55252,55555,56712] portvar SHELLCODE_PORTS !0 portvar ORACLE_PORTS 1024: portvar SSH_PORTS 22 portvar FTP_PORTS [21,2100,3535] portvar SIP_PORTS [5060,5061,5600] portvar FILE_DATA_PORTS [$HTTP_PORTS,110,143] portvar GTP_PORTS [2123,2152,3386] ipvar AIM_SERVERS [64.12.24.0/23,64.12.28.0/23,64.12.161.0/24,64.12.163.0/24,64.12.200.0/24,205.188.3.0/24,205.188.5.0/24,205.188.7.0/24,205.188.9.0/24,205.188.153.0/24,205.188.179.0/24,205.188.248.0/24] var RULE_PATH rules #var SO_RULE_PATH so_rules var PREPROC_RULE_PATH rules #var WHITE_LIST_PATH rules var BLACK_LIST_PATH rules config enable_decode_drops config enable_tcpopt_experimental_drops config enable_tcpopt_obsolete_drops config enable_tcpopt_ttcp_drops config enable_tcpopt_drops config enable_ipopt_drops config enable_decode_oversized_drops config policy_mode:inline #config checksum_mode: all config checksum_drop: all # config flowbits_size: 64 # config ignore_ports: tcp 21 6667:6671 1356 # config ignore_ports: udp 1:17 53 # config response: eth0 attempts 2 config daq: afpacket config daq_dir: /usr/lib/daq/ config daq_mode: inline config daq_var: buffer_size_mb=300 # config set_gid: # config set_uid: # config snaplen: # config bpf_file: config logdir: /tmp/snort/ config pcre_match_limit: 5000 config pcre_match_limit_recursion: 2500 config detection: search-method ac-nq search-optimize max-pattern-len 18 no_stream_inserts config event_queue: max_queue 8 log 5 order_events content_length # config enable_gtp #config ppm: max-pkt-time 250, \ # fastpath-expensive-packets, \ # pkt-log #config ppm: max-rule-time 200, \ # threshold 3, \ # suspend-expensive-rules, \ # suspend-timeout 20, \ # rule-log alert #config profile_rules: print all, sort avg_ticks #config profile_preprocs: print all, sort avg_ticks config paf_max: 16000 dynamicpreprocessor directory /usr/lib/snort_dynamicpreprocessor/ dynamicengine /usr/lib/snort_dynamicengine/libsf_engine.so #dynamicdetection directory /usr/local/lib/snort_dynamicrules # preprocessor gtp: ports { 2123 3386 2152 } preprocessor normalize_ip4 preprocessor normalize_tcp: ips ecn stream preprocessor normalize_icmp4 preprocessor normalize_ip6 preprocessor normalize_icmp6 preprocessor frag3_global: max_frags 65536 preprocessor frag3_engine: policy windows detect_anomalies overlap_limit 10 min_fragment_length 100 timeout 180 preprocessor stream5_global: track_tcp yes, \ track_udp yes, \ track_icmp yes, \ max_tcp 10000, \ max_udp 10000, \ memcap 9388608, \ max_active_responses 2, \ min_response_seconds 5, \ prune_log_max 2579067 preprocessor stream5_tcp: policy windows, detect_anomalies, require_3whs 180, \ overlap_limit 10, small_segments 3 bytes 150, timeout 180, \ max_queued_bytes 2550531, \ max_queued_segs 3621, \ ports client 21 22 23 25 42 53 70 79 109 110 111 113 119 135 136 137 139 143 \ 161 445 513 514 587 593 691 1433 1521 1741 2100 3306 6070 6665 6666 6667 6668 6669 \ 7000 8181 32770 32771 32772 32773 32774 32775 32776 32777 32778 32779, \ ports both 36 80 81 82 83 84 85 86 87 88 89 90 110 311 383 443 465 563 555 587 591 593 631 636 801 808 818 901 972 989 992 993 994 995 1158 1220 1414 1533 1741 1830 1942 2231 2301 2381 2809 2980 3029 3037 3057 3128 3443 3702 4000 4343 4848 5000 5117 5250 5600 6080 6173 6988 7907 7000 7001 7071 7144 7145 7510 7802 7770 7777 7778 7779 \ 7801 7900 7901 7902 7903 7904 7905 7906 7908 7909 7910 7911 7912 7913 7914 7915 7916 \ 7917 7918 7919 7920 8000 8008 8014 8028 8080 8081 8082 8085 8088 8090 8118 8123 8180 8181 8222 8243 8280 8300 8333 8344 8500 8509 8800 8888 8899 8983 9000 9060 9080 9090 9091 9111 9290 9443 9999 10000 11371 12601 13014 15489 29991 33300 34412 34443 34444 41080 44449 50000 50002 51423 53331 55252 55555 56712 preprocessor stream5_udp: timeout 180 #preprocessor perfmonitor: time 300 file /var/snort/snort.stats pktcnt 10000 preprocessor http_inspect: global iis_unicode_map unicode.map 1252 compress_depth 65535 decompress_depth 65535 preprocessor http_inspect_server: server default \ http_methods { GET POST PUT SEARCH MKCOL COPY MOVE LOCK UNLOCK NOTIFY POLL BCOPY BDELETE BMOVE LINK UNLINK OPTIONS HEAD DELETE TRACE TRACK CONNECT SOURCE SUBSCRIBE UNSUBSCRIBE PROPFIND PROPPATCH BPROPFIND BPROPPATCH RPC_CONNECT PROXY_SUCCESS BITS_POST CCM_POST SMS_POST RPC_IN_DATA RPC_OUT_DATA RPC_ECHO_DATA } \ chunk_length 500000 \ server_flow_depth 0 \ client_flow_depth 0 \ post_depth 65495 \ oversize_dir_length 500 \ max_header_length 750 \ max_headers 100 \ max_spaces 200 \ small_chunk_length { 10 5 } \ ports { 36 80 81 82 83 84 85 86 87 88 89 90 311 383 555 591 593 631 801 808 818 901 972 1158 1220 1414 1533 1741 1830 1942 2231 2301 2381 2809 2980 3029 3037 3057 3128 3443 3702 4000 4343 4848 5000 5117 5250 5600 6080 6173 6988 7000 7001 7071 7144 7145 7510 7770 7777 7778 7779 8000 8008 8014 8028 8080 8081 8082 8085 8088 8090 8118 8123 8180 8181 8222 8243 8280 8300 8333 8344 8500 8509 8800 8888 8899 8983 9000 9060 9080 9090 9091 9111 9290 9443 9999 10000 11371 12601 13014 15489 29991 33300 34412 34443 34444 41080 44449 50000 50002 51423 53331 55252 55555 56712 } \ non_rfc_char { 0x00 0x01 0x02 0x03 0x04 0x05 0x06 0x07 } \ enable_cookie \ extended_response_inspection \ inspect_gzip \ normalize_utf \ unlimited_decompress \ normalize_javascript \ apache_whitespace no \ ascii no \ bare_byte no \ directory no \ double_decode no \ iis_backslash no \ iis_delimiter no \ iis_unicode no \ multi_slash no \ utf_8 no \ u_encode yes \ webroot no preprocessor rpc_decode: 111 32770 32771 32772 32773 32774 32775 32776 32777 32778 32779 no_alert_multiple_requests no_alert_large_fragments no_alert_incomplete preprocessor bo #preprocessor ftp_telnet: global inspection_type stateful encrypted_traffic no check_encrypted #preprocessor ftp_telnet_protocol: telnet \ # ayt_attack_thresh 20 \ # normalize ports { 23 } \ # detect_anomalies #preprocessor ftp_telnet_protocol: ftp server default \ # def_max_param_len 100 \ # ports { 21 2100 3535 } \ # telnet_cmds yes \ # ignore_telnet_erase_cmds yes \ # ftp_cmds { ABOR ACCT ADAT ALLO APPE AUTH CCC CDUP } \ # ftp_cmds { CEL CLNT CMD CONF CWD DELE ENC EPRT } \ # ftp_cmds { EPSV ESTA ESTP FEAT HELP LANG LIST LPRT } \ # ftp_cmds { LPSV MACB MAIL MDTM MIC MKD MLSD MLST } \ # ftp_cmds { MODE NLST NOOP OPTS PASS PASV PBSZ PORT } \ # ftp_cmds { PROT PWD QUIT REIN REST RETR RMD RNFR } \ # ftp_cmds { RNTO SDUP SITE SIZE SMNT STAT STOR STOU } \ # ftp_cmds { STRU SYST TEST TYPE USER XCUP XCRC XCWD } \ # ftp_cmds { XMAS XMD5 XMKD XPWD XRCP XRMD XRSQ XSEM } \ # ftp_cmds { XSEN XSHA1 XSHA256 } \ # alt_max_param_len 0 { ABOR CCC CDUP ESTA FEAT LPSV NOOP PASV PWD QUIT REIN STOU SYST XCUP XPWD } \ # alt_max_param_len 200 { ALLO APPE CMD HELP NLST RETR RNFR STOR STOU XMKD } \ # alt_max_param_len 256 { CWD RNTO } \ # alt_max_param_len 400 { PORT } \ # alt_max_param_len 512 { SIZE } \ # chk_str_fmt { ACCT ADAT ALLO APPE AUTH CEL CLNT CMD } \ # chk_str_fmt { CONF CWD DELE ENC EPRT EPSV ESTP HELP } \ # chk_str_fmt { LANG LIST LPRT MACB MAIL MDTM MIC MKD } \ # chk_str_fmt { MLSD MLST MODE NLST OPTS PASS PBSZ PORT } \ # chk_str_fmt { PROT REST RETR RMD RNFR RNTO SDUP SITE } \ # chk_str_fmt { SIZE SMNT STAT STOR STRU TEST TYPE USER } \ # chk_str_fmt { XCRC XCWD XMAS XMD5 XMKD XRCP XRMD XRSQ } \ # chk_str_fmt { XSEM XSEN XSHA1 XSHA256 } \ # cmd_validity ALLO < int [ char R int ] > \ # cmd_validity EPSV < [ { char 12 | char A char L char L } ] > \ # cmd_validity MACB < string > \ # cmd_validity MDTM < [ date nnnnnnnnnnnnnn[.n[n[n]]] ] string > \ # cmd_validity MODE < char ASBCZ > \ # cmd_validity PORT < host_port > \ # cmd_validity PROT < char CSEP > \ # cmd_validity STRU < char FRPO [ string ] > \ # cmd_validity TYPE < { char AE [ char NTC ] | char I | char L [ number ] } > #preprocessor ftp_telnet_protocol: ftp client default \ # max_resp_len 256 \ # bounce yes \ # ignore_telnet_erase_cmds yes \ # telnet_cmds yes #preprocessor smtp: ports { 25 465 587 691 } \ # inspection_type stateful \ # b64_decode_depth 0 \ # qp_decode_depth 0 \ # bitenc_decode_depth 0 \ # uu_decode_depth 0 \ # log_mailfrom \ # log_rcptto \ # log_filename \ # log_email_hdrs \ # normalize cmds \ # normalize_cmds { ATRN AUTH BDAT CHUNKING DATA DEBUG EHLO EMAL ESAM ESND ESOM ETRN EVFY } \ # normalize_cmds { EXPN HELO HELP IDENT MAIL NOOP ONEX QUEU QUIT RCPT RSET SAML SEND SOML } \ # normalize_cmds { STARTTLS TICK TIME TURN TURNME VERB VRFY X-ADAT X-DRCP X-ERCP X-EXCH50 } \ # normalize_cmds { X-EXPS X-LINK2STATE XADR XAUTH XCIR XEXCH50 XGEN XLICENSE XQUE XSTA XTRN XUSR } \ # max_command_line_len 512 \ # max_header_line_len 1000 \ # max_response_line_len 512 \ # alt_max_command_line_len 260 { MAIL } \ # alt_max_command_line_len 300 { RCPT } \ # alt_max_command_line_len 500 { HELP HELO ETRN EHLO } \ # alt_max_command_line_len 255 { EXPN VRFY ATRN SIZE BDAT DEBUG EMAL ESAM ESND ESOM EVFY IDENT NOOP RSET } \ # alt_max_command_line_len 246 { SEND SAML SOML AUTH TURN ETRN DATA RSET QUIT ONEX QUEU STARTTLS TICK TIME TURNME VERB X-EXPS X-LINK2STATE XADR XAUTH XCIR XEXCH50 XGEN XLICENSE XQUE XSTA XTRN XUSR } \ # valid_cmds { ATRN AUTH BDAT CHUNKING DATA DEBUG EHLO EMAL ESAM ESND ESOM ETRN EVFY } \ # valid_cmds { EXPN HELO HELP IDENT MAIL NOOP ONEX QUEU QUIT RCPT RSET SAML SEND SOML } \ # valid_cmds { STARTTLS TICK TIME TURN TURNME VERB VRFY X-ADAT X-DRCP X-ERCP X-EXCH50 } \ # valid_cmds { X-EXPS X-LINK2STATE XADR XAUTH XCIR XEXCH50 XGEN XLICENSE XQUE XSTA XTRN XUSR } \ # xlink2state { enabled } #preprocessor sfportscan: proto { all } memcap { 500000 } sense_level { medium } # preprocessor arpspoof # preprocessor arpspoof_detect_host: 192.168.40.1 f0:0f:00:f0:0f:00 #preprocessor ssh: server_ports { 22 } \ # autodetect \ # max_client_bytes 19600 \ # max_encrypted_packets 20 \ # max_server_version_len 100 \ # enable_respoverflow enable_ssh1crc32 \ # enable_srvoverflow enable_protomismatch #preprocessor dcerpc2: memcap 102400, events [co ] #preprocessor dcerpc2_server: default, policy WinXP, \ # detect [smb [139,445], tcp 135, udp 135, rpc-over-http-server 593], \ # autodetect [tcp 1025:, udp 1025:, rpc-over-http-server 1025:], \ # smb_max_chain 3, smb_invalid_shares ["C$", "D$", "ADMIN$"] #preprocessor dns: ports { 53 } enable_rdata_overflow preprocessor ssl: ports { 443 465 563 587 636 989 992 993 994 995 7801 7802 7900 7901 7902 7903 7904 7905 7906 7907 7908 7909 7910 7911 7912 7913 7914 7915 7916 7917 7918 7919 7920 }, trustservers, noinspect_encrypted #preprocessor sensitive_data: alert_threshold 25 #preprocessor sip: max_sessions 1024, \ # ports { 5060 5061 5600 }, \ # methods { invite \ # cancel \ # ack \ # bye \ # register \ # options \ # refer \ # subscribe \ # update \ # join \ # info \ # message \ # notify \ # benotify \ # do \ # qauth \ # sprack \ # publish \ # service \ # unsubscribe \ # prack }, \ # max_uri_len 512, \ # max_call_id_len 80, \ # max_requestName_len 20, \ # max_from_len 256, \ # max_to_len 256, \ # max_via_len 1024, \ # max_contact_len 512, \ # max_content_len 2048 #preprocessor imap: \ # ports { 143 } \ # b64_decode_depth 0 \ # qp_decode_depth 0 \ # bitenc_decode_depth 0 \ # uu_decode_depth 0 #preprocessor pop: \ # ports { 110 } \ # b64_decode_depth 0 \ # qp_decode_depth 0 \ # bitenc_decode_depth 0 \ # uu_decode_depth 0 #preprocessor modbus: ports { 502 } #preprocessor dnp3: ports { 20000 } \ # memcap 131077 \ # check_crc #preprocessor reputation: \ # memcap 100, \ # priority whitelist, \ # nested_ip inner, \ # whitelist $WHITE_LIST_PATH/white_list.rules, \ # blacklist $BLACK_LIST_PATH/L2.blacklist # output unified2: filename merged.log, limit 128, nostamp, mpls_event_types, vlan_event_types # output alert_unified2: filename snort.alert, limit 128, nostamp # output log_unified2: filename snort.log, limit 128, nostamp output alert_fast: alert.fast 64K # output log_tcpdump: tcpdump.log include classification.config include reference.config include reference.config include $RULE_PATH/local.rules include $RULE_PATH/snort.rules #include $PREPROC_RULE_PATH/preprocessor.rules #include $PREPROC_RULE_PATH/decoder.rules #include $PREPROC_RULE_PATH/sensitive-data.rules # include $SO_RULE_PATH/so1.rules # include $SO_RULE_PATH/so2-misc.rules include threshold.conf ------------------------------- Now, go to /usr/lib/snort_dynamicpreprocessor and delete all but the three libsf_ssl_preproc* Reboot. It's always wise to always reboot via the GUI or CLI reboot -f vs pulling the plug.
Running the latest OpenWrt stable release
|
|
Hi user8446,
I'm lurking this thread and trying out the various recommendations you're providing. Greatly appreciated! I'm also getting the memcap threshold error in my log. After implementing this above and reboot, I'm seeing a lot of this error now: Mon Nov 7 09:16:24 2016 daemon.crit dnsmasq[5764]: illegal repeated keyword at line 13 of /var/etc/dnsmasq.conf Mon Nov 7 09:16:24 2016 daemon.crit dnsmasq[5764]: FAILED to start up My dnsmasq.conf looks like this: # auto-generated config file from /etc/config/dhcp conf-file=/etc/dnsmasq.conf dhcp-authoritative domain-needed log-queries localise-queries read-ethers bogus-priv expand-hosts local-service domain=lan server=/lan/ dhcp-leasefile=/tmp/dhcp.leases resolv-file=/tmp/resolv.conf.auto addn-hosts=/tmp/hosts conf-dir=/tmp/dnsmasq.d stop-dns-rebind rebind-localhost-ok dhcp-broadcast=tag:needs-broadcast no-dhcp-interface=br-lan with line 13 the dhcp-leasfile=/tmp/dhcp.leases (or is the first line with # not counted? and its the "resolv-file="?) The file /tmp/dhcp.leases does exist, but is an empty file of 0 kb. If I manually restart dnsmasq via LUCI interface the log shows the same error for 6 cycles. Any recommendations? TIA for all your help.
Shield Pro v1, Chaos Calmer, FW 1.51 SP1, v8.3.2, Bridge Mode
|
|
In reply to this post by user8446
HI, user8446 where do I put this ? sorry getting rusty
thanks for all the help ipvar HOME_NET any ipvar EXTERNAL_NET any ipvar DNS_SERVERS $HOME_NET ipvar SMTP_SERVERS $HOME_NET ipvar HTTP_SERVERS $HOME_NET ipvar SQL_SERVERS [192.168.0.0/16,10.0.0.0/8,172.16.0.0/12] ipvar TELNET_SERVERS $HOME_NET ipvar SSH_SERVERS $HOME_NET ipvar FTP_SERVERS $HOME_NET ipvar SIP_SERVERS $HOME_NET portvar HTTP_PORTS [36,80,81,82,83,84,85,86,87,88,89,90,311,383,555,591,593,631,801,808,818,901,972,1158,1220,1414,1533,1741,1830,1942,2231,2301,2381,2809,2980,3029,3037,3057,3128,3443,3702,4000,4343,4848,5000,5117,5250,5600,6080,6173,6988,7000,7001,7071,7144,7145,7510,7770,7777,7778,7779,8000,8008,8014,8028,8080,8081,8082,8085,8088,8090,8118,8123,8180,8181,8222,8243,8280,8300,8333,8344,8500,8509,8800,8888,8899,8983,9000,9060,9080,9090,9091,9111,9290,9443,9999,10000,11371,12601,13014,15489,29991,33300,34412,34443,34444,41080,44449,50000,50002,51423,53331,55252,55555,56712] portvar SHELLCODE_PORTS !0 portvar ORACLE_PORTS 1024: portvar SSH_PORTS 22 portvar FTP_PORTS [21,2100,3535] portvar SIP_PORTS [5060,5061,5600] portvar FILE_DATA_PORTS [$HTTP_PORTS,110,143] portvar GTP_PORTS [2123,2152,3386] ipvar AIM_SERVERS [64.12.24.0/23,64.12.28.0/23,64.12.161.0/24,64.12.163.0/24,64.12.200.0/24,205.188.3.0/24,205.188.5.0/24,205.188.7.0/24,205.188.9.0/24,205.188.153.0/24,205.188.179.0/24,205.188.248.0/24] var RULE_PATH rules #var SO_RULE_PATH so_rules var PREPROC_RULE_PATH rules #var WHITE_LIST_PATH rules var BLACK_LIST_PATH rules config enable_decode_drops config enable_tcpopt_experimental_drops config enable_tcpopt_obsolete_drops config enable_tcpopt_ttcp_drops config enable_tcpopt_drops config enable_ipopt_drops config enable_decode_oversized_drops config policy_mode:inline #config checksum_mode: all config checksum_drop: all # config flowbits_size: 64 # config ignore_ports: tcp 21 6667:6671 1356 # config ignore_ports: udp 1:17 53 # config response: eth0 attempts 2 config daq: afpacket config daq_dir: /usr/lib/daq/ config daq_mode: inline config daq_var: buffer_size_mb=300 # config set_gid: # config set_uid: # config snaplen: # config bpf_file: config logdir: /tmp/snort/ config pcre_match_limit: 5000 config pcre_match_limit_recursion: 2500 config detection: search-method ac-nq search-optimize max-pattern-len 18 no_stream_inserts config event_queue: max_queue 8 log 5 order_events content_length # config enable_gtp #config ppm: max-pkt-time 250, \ # fastpath-expensive-packets, \ # pkt-log #config ppm: max-rule-time 200, \ # threshold 3, \ # suspend-expensive-rules, \ # suspend-timeout 20, \ # rule-log alert #config profile_rules: print all, sort avg_ticks #config profile_preprocs: print all, sort avg_ticks config paf_max: 16000 dynamicpreprocessor directory /usr/lib/snort_dynamicpreprocessor/ dynamicengine /usr/lib/snort_dynamicengine/libsf_engine.so #dynamicdetection directory /usr/local/lib/snort_dynamicrules # preprocessor gtp: ports { 2123 3386 2152 } preprocessor normalize_ip4 preprocessor normalize_tcp: ips ecn stream preprocessor normalize_icmp4 preprocessor normalize_ip6 preprocessor normalize_icmp6 preprocessor frag3_global: max_frags 65536 preprocessor frag3_engine: policy windows detect_anomalies overlap_limit 10 min_fragment_length 100 timeout 180 preprocessor stream5_global: track_tcp yes, \ track_udp yes, \ track_icmp yes, \ max_tcp 10000, \ max_udp 10000, \ memcap 9388608, \ max_active_responses 2, \ min_response_seconds 5, \ prune_log_max 2579067 preprocessor stream5_tcp: policy windows, detect_anomalies, require_3whs 180, \ overlap_limit 10, small_segments 3 bytes 150, timeout 180, \ max_queued_bytes 2550531, \ max_queued_segs 3621, \ ports client 21 22 23 25 42 53 70 79 109 110 111 113 119 135 136 137 139 143 \ 161 445 513 514 587 593 691 1433 1521 1741 2100 3306 6070 6665 6666 6667 6668 6669 \ 7000 8181 32770 32771 32772 32773 32774 32775 32776 32777 32778 32779, \ ports both 36 80 81 82 83 84 85 86 87 88 89 90 110 311 383 443 465 563 555 587 591 593 631 636 801 808 818 901 972 989 992 993 994 995 1158 1220 1414 1533 1741 1830 1942 2231 2301 2381 2809 2980 3029 3037 3057 3128 3443 3702 4000 4343 4848 5000 5117 5250 5600 6080 6173 6988 7907 7000 7001 7071 7144 7145 7510 7802 7770 7777 7778 7779 \ 7801 7900 7901 7902 7903 7904 7905 7906 7908 7909 7910 7911 7912 7913 7914 7915 7916 \ 7917 7918 7919 7920 8000 8008 8014 8028 8080 8081 8082 8085 8088 8090 8118 8123 8180 8181 8222 8243 8280 8300 8333 8344 8500 8509 8800 8888 8899 8983 9000 9060 9080 9090 9091 9111 9290 9443 9999 10000 11371 12601 13014 15489 29991 33300 34412 34443 34444 41080 44449 50000 50002 51423 53331 55252 55555 56712 preprocessor stream5_udp: timeout 180 #preprocessor perfmonitor: time 300 file /var/snort/snort.stats pktcnt 10000 preprocessor http_inspect: global iis_unicode_map unicode.map 1252 compress_depth 65535 decompress_depth 65535 preprocessor http_inspect_server: server default \ http_methods { GET POST PUT SEARCH MKCOL COPY MOVE LOCK UNLOCK NOTIFY POLL BCOPY BDELETE BMOVE LINK UNLINK OPTIONS HEAD DELETE TRACE TRACK CONNECT SOURCE SUBSCRIBE UNSUBSCRIBE PROPFIND PROPPATCH BPROPFIND BPROPPATCH RPC_CONNECT PROXY_SUCCESS BITS_POST CCM_POST SMS_POST RPC_IN_DATA RPC_OUT_DATA RPC_ECHO_DATA } \ chunk_length 500000 \ server_flow_depth 0 \ client_flow_depth 0 \ post_depth 65495 \ oversize_dir_length 500 \ max_header_length 750 \ max_headers 100 \ max_spaces 200 \ small_chunk_length { 10 5 } \ ports { 36 80 81 82 83 84 85 86 87 88 89 90 311 383 555 591 593 631 801 808 818 901 972 1158 1220 1414 1533 1741 1830 1942 2231 2301 2381 2809 2980 3029 3037 3057 3128 3443 3702 4000 4343 4848 5000 5117 5250 5600 6080 6173 6988 7000 7001 7071 7144 7145 7510 7770 7777 7778 7779 8000 8008 8014 8028 8080 8081 8082 8085 8088 8090 8118 8123 8180 8181 8222 8243 8280 8300 8333 8344 8500 8509 8800 8888 8899 8983 9000 9060 9080 9090 9091 9111 9290 9443 9999 10000 11371 12601 13014 15489 29991 33300 34412 34443 34444 41080 44449 50000 50002 51423 53331 55252 55555 56712 } \ non_rfc_char { 0x00 0x01 0x02 0x03 0x04 0x05 0x06 0x07 } \ enable_cookie \ extended_response_inspection \ inspect_gzip \ normalize_utf \ unlimited_decompress \ normalize_javascript \ apache_whitespace no \ ascii no \ bare_byte no \ directory no \ double_decode no \ iis_backslash no \ iis_delimiter no \ iis_unicode no \ multi_slash no \ utf_8 no \ u_encode yes \ webroot no preprocessor rpc_decode: 111 32770 32771 32772 32773 32774 32775 32776 32777 32778 32779 no_alert_multiple_requests no_alert_large_fragments no_alert_incomplete preprocessor bo #preprocessor ftp_telnet: global inspection_type stateful encrypted_traffic no check_encrypted #preprocessor ftp_telnet_protocol: telnet \ # ayt_attack_thresh 20 \ # normalize ports { 23 } \ # detect_anomalies #preprocessor ftp_telnet_protocol: ftp server default \ # def_max_param_len 100 \ # ports { 21 2100 3535 } \ # telnet_cmds yes \ # ignore_telnet_erase_cmds yes \ # ftp_cmds { ABOR ACCT ADAT ALLO APPE AUTH CCC CDUP } \ # ftp_cmds { CEL CLNT CMD CONF CWD DELE ENC EPRT } \ # ftp_cmds { EPSV ESTA ESTP FEAT HELP LANG LIST LPRT } \ # ftp_cmds { LPSV MACB MAIL MDTM MIC MKD MLSD MLST } \ # ftp_cmds { MODE NLST NOOP OPTS PASS PASV PBSZ PORT } \ # ftp_cmds { PROT PWD QUIT REIN REST RETR RMD RNFR } \ # ftp_cmds { RNTO SDUP SITE SIZE SMNT STAT STOR STOU } \ # ftp_cmds { STRU SYST TEST TYPE USER XCUP XCRC XCWD } \ # ftp_cmds { XMAS XMD5 XMKD XPWD XRCP XRMD XRSQ XSEM } \ # ftp_cmds { XSEN XSHA1 XSHA256 } \ # alt_max_param_len 0 { ABOR CCC CDUP ESTA FEAT LPSV NOOP PASV PWD QUIT REIN STOU SYST XCUP XPWD } \ # alt_max_param_len 200 { ALLO APPE CMD HELP NLST RETR RNFR STOR STOU XMKD } \ # alt_max_param_len 256 { CWD RNTO } \ # alt_max_param_len 400 { PORT } \ # alt_max_param_len 512 { SIZE } \ # chk_str_fmt { ACCT ADAT ALLO APPE AUTH CEL CLNT CMD } \ # chk_str_fmt { CONF CWD DELE ENC EPRT EPSV ESTP HELP } \ # chk_str_fmt { LANG LIST LPRT MACB MAIL MDTM MIC MKD } \ # chk_str_fmt { MLSD MLST MODE NLST OPTS PASS PBSZ PORT } \ # chk_str_fmt { PROT REST RETR RMD RNFR RNTO SDUP SITE } \ # chk_str_fmt { SIZE SMNT STAT STOR STRU TEST TYPE USER } \ # chk_str_fmt { XCRC XCWD XMAS XMD5 XMKD XRCP XRMD XRSQ } \ # chk_str_fmt { XSEM XSEN XSHA1 XSHA256 } \ # cmd_validity ALLO < int [ char R int ] > \ # cmd_validity EPSV < [ { char 12 | char A char L char L } ] > \ # cmd_validity MACB < string > \ # cmd_validity MDTM < [ date nnnnnnnnnnnnnn[.n[n[n]]] ] string > \ # cmd_validity MODE < char ASBCZ > \ # cmd_validity PORT < host_port > \ # cmd_validity PROT < char CSEP > \ # cmd_validity STRU < char FRPO [ string ] > \ # cmd_validity TYPE < { char AE [ char NTC ] | char I | char L [ number ] } > #preprocessor ftp_telnet_protocol: ftp client default \ # max_resp_len 256 \ # bounce yes \ # ignore_telnet_erase_cmds yes \ # telnet_cmds yes #preprocessor smtp: ports { 25 465 587 691 } \ # inspection_type stateful \ # b64_decode_depth 0 \ # qp_decode_depth 0 \ # bitenc_decode_depth 0 \ # uu_decode_depth 0 \ # log_mailfrom \ # log_rcptto \ # log_filename \ # log_email_hdrs \ # normalize cmds \ # normalize_cmds { ATRN AUTH BDAT CHUNKING DATA DEBUG EHLO EMAL ESAM ESND ESOM ETRN EVFY } \ # normalize_cmds { EXPN HELO HELP IDENT MAIL NOOP ONEX QUEU QUIT RCPT RSET SAML SEND SOML } \ # normalize_cmds { STARTTLS TICK TIME TURN TURNME VERB VRFY X-ADAT X-DRCP X-ERCP X-EXCH50 } \ # normalize_cmds { X-EXPS X-LINK2STATE XADR XAUTH XCIR XEXCH50 XGEN XLICENSE XQUE XSTA XTRN XUSR } \ # max_command_line_len 512 \ # max_header_line_len 1000 \ # max_response_line_len 512 \ # alt_max_command_line_len 260 { MAIL } \ # alt_max_command_line_len 300 { RCPT } \ # alt_max_command_line_len 500 { HELP HELO ETRN EHLO } \ # alt_max_command_line_len 255 { EXPN VRFY ATRN SIZE BDAT DEBUG EMAL ESAM ESND ESOM EVFY IDENT NOOP RSET } \ # alt_max_command_line_len 246 { SEND SAML SOML AUTH TURN ETRN DATA RSET QUIT ONEX QUEU STARTTLS TICK TIME TURNME VERB X-EXPS X-LINK2STATE XADR XAUTH XCIR XEXCH50 XGEN XLICENSE XQUE XSTA XTRN XUSR } \ # valid_cmds { ATRN AUTH BDAT CHUNKING DATA DEBUG EHLO EMAL ESAM ESND ESOM ETRN EVFY } \ # valid_cmds { EXPN HELO HELP IDENT MAIL NOOP ONEX QUEU QUIT RCPT RSET SAML SEND SOML } \ # valid_cmds { STARTTLS TICK TIME TURN TURNME VERB VRFY X-ADAT X-DRCP X-ERCP X-EXCH50 } \ # valid_cmds { X-EXPS X-LINK2STATE XADR XAUTH XCIR XEXCH50 XGEN XLICENSE XQUE XSTA XTRN XUSR } \ # xlink2state { enabled } #preprocessor sfportscan: proto { all } memcap { 500000 } sense_level { medium } # preprocessor arpspoof # preprocessor arpspoof_detect_host: 192.168.40.1 f0:0f:00:f0:0f:00 #preprocessor ssh: server_ports { 22 } \ # autodetect \ # max_client_bytes 19600 \ # max_encrypted_packets 20 \ # max_server_version_len 100 \ # enable_respoverflow enable_ssh1crc32 \ # enable_srvoverflow enable_protomismatch #preprocessor dcerpc2: memcap 102400, events [co ] #preprocessor dcerpc2_server: default, policy WinXP, \ # detect [smb [139,445], tcp 135, udp 135, rpc-over-http-server 593], \ # autodetect [tcp 1025:, udp 1025:, rpc-over-http-server 1025:], \ # smb_max_chain 3, smb_invalid_shares ["C$", "D$", "ADMIN$"] #preprocessor dns: ports { 53 } enable_rdata_overflow preprocessor ssl: ports { 443 465 563 587 636 989 992 993 994 995 7801 7802 7900 7901 7902 7903 7904 7905 7906 7907 7908 7909 7910 7911 7912 7913 7914 7915 7916 7917 7918 7919 7920 }, trustservers, noinspect_encrypted #preprocessor sensitive_data: alert_threshold 25 #preprocessor sip: max_sessions 1024, \ # ports { 5060 5061 5600 }, \ # methods { invite \ # cancel \ # ack \ # bye \ # register \ # options \ # refer \ # subscribe \ # update \ # join \ # info \ # message \ # notify \ # benotify \ # do \ # qauth \ # sprack \ # publish \ # service \ # unsubscribe \ # prack }, \ # max_uri_len 512, \ # max_call_id_len 80, \ # max_requestName_len 20, \ # max_from_len 256, \ # max_to_len 256, \ # max_via_len 1024, \ # max_contact_len 512, \ # max_content_len 2048 #preprocessor imap: \ # ports { 143 } \ # b64_decode_depth 0 \ # qp_decode_depth 0 \ # bitenc_decode_depth 0 \ # uu_decode_depth 0 #preprocessor pop: \ # ports { 110 } \ # b64_decode_depth 0 \ # qp_decode_depth 0 \ # bitenc_decode_depth 0 \ # uu_decode_depth 0 #preprocessor modbus: ports { 502 } #preprocessor dnp3: ports { 20000 } \ # memcap 131077 \ # check_crc #preprocessor reputation: \ # memcap 100, \ # priority whitelist, \ # nested_ip inner, \ # whitelist $WHITE_LIST_PATH/white_list.rules, \ # blacklist $BLACK_LIST_PATH/L2.blacklist # output unified2: filename merged.log, limit 128, nostamp, mpls_event_types, vlan_event_types # output alert_unified2: filename snort.alert, limit 128, nostamp # output log_unified2: filename snort.log, limit 128, nostamp output alert_fast: alert.fast 64K # output log_tcpdump: tcpdump.log include classification.config include reference.config include reference.config include $RULE_PATH/local.rules include $RULE_PATH/snort.rules #include $PREPROC_RULE_PATH/preprocessor.rules #include $PREPROC_RULE_PATH/decoder.rules #include $PREPROC_RULE_PATH/sensitive-data.rules # include $SO_RULE_PATH/so1.rules # include $SO_RULE_PATH/so2-misc.rules include threshold.conf |
|
Jumping in for user8446,
Breda, that is a new snort.conf file. You can find it in /etc/snort on the Shield. i.e. /etc/snort/snort.conf. Rename your existing snort.conf file to something like snort.conf.sav or snort.conf.bak and then copy/paste the text user8446 provided above into a new snort.conf file. I use Notepad++ for generating these types of files. You can use WinSCP to help copy them back and forth from your PC to the Shield. Good luck!
Shield Pro v1, Chaos Calmer, FW 1.51 SP1, v8.3.2, Bridge Mode
|
«
Return to Technical Discussion
|
1 view|%1 views
| Free forum by Nabble | Edit this page |

