[FIRMWARE] Itus Shield v2
12345
... 7
12345
... 7
|
Administrator
|
Well, it doesn't look like they have any sensors, thermal or otherwise, on the board..
root@OpenWrt:/tmp# sensors
|
|
Administrator
|
I added Python3 support to the image, but it added an additional 30MB of size (currently, this image is around 110MB in size right now!), so I'm not sure if it'll be wise to KEEP it or not.. Something that can be discussed..
I've had time to go combing through MIPS patches (going back to 2011!) for the Octeon platform. Unfortunately, they've got to be gone thru manually, so it takes a while.. And, they were designed for the mainline kernel at the time the patch was released, so it doesn't always work out well. We will get there :)
Running Itus Shield v2 Firmware
|
|
Administrator
|
So, as I mentioned very early on, I have no real experience with OpenWrt,, or router firmware in general.. My background is in Infosec and I did custom Android ROMs back before Google decided to lock it down.
That being said, I've been expanding my knowledge base (always awesome), but it means I'm feeling my way thru the darkness at times. This is one of those times.. I recently got introduced to binwalk, which allows me to dig into the ELF-binary files the Shield uses.. One of the things I just noticed.. The original images from Itus are LITTLE-ENDIAN built.. The images I'm building a BIG-ENDIAN.. I'm not sure exactly the difference is (except the most vs least significant bits) programmatically or what effects it might have.. I don't SEE an issue in things so far, but I've always built it as BE.. Does anyone have an info they can share on this and which might be better for a mips64 system?
Running Itus Shield v2 Firmware
|
|
Administrator
|
Few updates:
I updated my Ubuntu from 19.10 to 20.04, and in the process, completely screwed my system. Yay! Luckily, I was thinking ahead and made the commit changes before hand. It did mean I completely lost everything on that drive, so I spent the evening rebuilding for compiling only to realize I never commited the .config file.. Anyway, I believe I've got the rebuild complete and I BELIEVE I re-included everything package wise, but the image file is about 15-20MB smaller than it was, so, I'll find out if I missed anything soon enough. To that end, I'm going to close out the Router stuff. Any other changes will most likely be configuration changes on the Shield itself after installing the image. Anyone who is testing, if you have changes you think should be included by default in the router image, let me know. Now, I think I'm going to start working on Bridge mode. It'll mean having to redo my network settings, but should be do-able. Just so I understand how Itus was doing it: Bridge mode is transparent and uses eth0/eth2 as the bridge and eth1 as the administrative interface?
Running Itus Shield v2 Firmware
|
|
Administrator
|
I don't know what happened to the forum, but the permissions were changed. I've corrected this.
The build laptop is still in pieces, I'm awaiting a new boot m.2 and a internal cable. Once it's back together, I'll start working on bridge mode in earnest. I've got the network config for it already figured out, but I want to look into some things like port-mirroring with packet scanning rather than snort for the bridge. I just can't do anything until I can compile again. Hopefully by the weekend! In case anyone feels like messing around with bridge mode: This is the uci network config. It bridges eth0/eth2 and pulls a DHCP IP for administrator from eth1 (you can static this, but I'll leave it to the end-user since I can't be sure what IP range they'd be using)
|
|
still seems broken Grommish, I tried to respond to the post but got a box asking me to justify why I needed to respond (or similar) :) Anyway - really glad your looking at Bridge mode as that is how I would actually use this again in my network :) All the best On Thu, 4 Jun 2020 at 06:11, Grommish [via Itus Networks Owners Forum] <[hidden email]> wrote: I don't know what happened to the forum, but the permissions were changed. I've corrected this.
Running v2 Firmware
|
|
Administrator
|
As you can see, I think I got it this time. Oy.. I still don't know why it happened, but oh well..
Running Itus Shield v2 Firmware
|
|
I just replied to the email, rather than using the site :) On Thu, 4 Jun 2020 at 09:34, Grommish [via Itus Networks Owners Forum] <[hidden email]> wrote: As you can see, I think I got it this time. Oy.. I still don't know why it happened, but oh well..
Running v2 Firmware
|
|
Administrator
|
Hey all.
So, I've been approaching this whole project as an end project, rather than as a means for someone to get to an end. Basically, I've been trying to build specific things rather than setting it up so the end-user can just do whatever they feel like.. Silly me :) With the fact my system grenaded, and that I had to re-install everything anyway.. I've got a base router image to work with. It is significantly smaller in size (32mb, i think?), the network is significantly FASTER (I had to redo the patches), and has absolutely no packages installed.. no banip, no adblock, no snort. It has luCi and a few applications I deemed critical enough (like tcpdump, ethtool, bridge-tools, etc). I will do something similar for the bridge mode. I'm going to play with the SDK and imagebuilder to allow anyone to roll their own at any time without build tools.. Then, only the base would need to be updated from time to time. Maybe see about hosting the entire compiled repo on github so opkg can work? Thoughts or comments?
Running Itus Shield v2 Firmware
|
|
Administrator
|
BTW, When i say the network is Significantly faster..
Transferring the router image to the device via SCP was seeing transfer speeds ranging from 600k-4.5MB/sec depending on how I messed with the drivers and which patches got put in..
|
|
In reply to this post by Grommish
Hi Grommish, I'm not sure that you had completely the wrong idea.. The Shield was originally advertised on Kickstarter as more of a "set & forget" style of appliance - i.e. one that handled automatic rule updates, etc - without needing to regularly login or tweak. I'd guess that like myself, many of who's left only started down the tinkering route out of necessity once Itus shut down. So personally, given that I've got a replacement device on pre-order to (hopefully) serve the original purpose, I'm unlikely to be doing too much more development. But if there was a router image with some form of reasonably stable self-updating security rules - DNS, Snort, or other firewall - then I'd be happy to install & use it, help with feedback & testing. Ad-block would be a bonus, but not necessary. That said, out of who's left, you've probably got a higher proportion with more tinker passion left than me ;) so hopefully they'll reply too. You've been doing brilliant work with the Shield to get it to this point - far beyond what I'd know how to do with my limited linux navigation skills - so I hope you can keep it going! On Thu, 11 Jun 2020 at 08:38, Grommish [via Itus Networks Owners Forum] <[hidden email]> wrote: Hey all.
OpenWrt SNAPSHOT, r10391-3d8d528939
|
|
Administrator
|
Thanks Gnomad.
I went into this without ever having used OpenWrt and long after Itus went under. I've got no experience with using the Shield in any way like Itus expected. As for your tinkering abilities, you got it loaded, so they aren't bad :p I'm still learning how the Shield architecture works. For example, from what I can tell, there is no way to update the kernel. It seem the board is set to boot from uBoot to the ELF-bin, which has the kernel. Once that is loaded, it boots like a Linux Live CD install. About halfway through the boot, when the MMC device finally comes up, the root pivots to whatever the proper partition is (as set by the front-panel switch). So, by the time the console goes active, / is mounted to /dev/mmcblk1p2 (for router). Ok, that works well.. I don't know if that is what is needed or proper, but it is what Itus did. Ok, so in order to update the kernel, you replace the ItusrouterImage and reboot. Not ideal, because it takes the box offline, but we aren't talking daily updates or anything. The issue comes when you have kernel-dependent libraries, which are stored on the mmc.. At that point, you've got kernel panics and dumps and a bootloop.. Ok, so.. This is why there is a /.norwits file and why everything gets wiped and recopied to the MMC.. But.. it wipes out USER data in it's present form. But, since we can't use the official opkg repos for OpenWrt, I'd have to either include them in the image anyway, or maintain a repo of all the compiled opkgs a user might want and their dependencies - For each published build with a library or kernel change. Even something like snort might throw a fit at having a kernel change and not being updated with a recompiled binary under the new version.. I don' t know yet.. Of course, this all could be the complete WRONG way to do it, but it's how Itus did it, so it was a starting point. There could be a "turnkey" image, but built on what? More issues I'm running into at the practicality sides of the Shield. Again, I have to put out there I've NEVER used the Shield as a security device.. I didn't even open the box from the Kickstarter until Jan 2019 because I lost the box :D More considerations I've had along the way. I'm not sure how effective a consumer-level security device would be. You can run snort3 all day long, but it won't touch encrypted traffic AFAIK. So, https breaks snort (or ssh, scp, etc). Not without other changes like an enforced TLS proxy to act as the encryption endpoints. What package should I look into? Will the shield have enough go-juice to handle it? At the very least, it's a badass little router that runs OpenWrt, but what else can it do? Cavium is impossible to get much out of. I've got their toolchain and kernel repos, but the toolchain refuses to build out and I can't get it to tell me why..
|
|
Cheers Grommish, appreciate you surveying this info! My main desires from the Shield would be something turnkey that can help protect all devices on a home network (not just computers & cellphones). In particular I'm concerned that smart-home appliances receive infrequent updates and expose ports or vulnerabilities I'm not aware of. And unlike web-browsing where I can control traffic using ad & script blocker plugins, I have basically zero control over their traffic. So, my priorities in an image: 1. Router mode, so it sits in front of all traffic. 2. Snort, with self-updating community rules as a baseline. (v2 or v3 https://snort.org/downloads/community/snort3-community-rules.tar.gz). Snort is much more than http inspection - e.g. see the list under the Readme section of https://snort.org/faq. Still very relevant according to https://tacticalflex.zendesk.com/hc/en-us/articles/360010678893-Snort-vs-Suricata - and still evolving since that article, moving to v3, etc. 3. Self-updating DNS rules a "nice to have". Noting that they'll start to lose some of their utility for general web browsing as DNS over HTTPS becomes more prevalent. 4. User-friendly means to setup a VPN and rules to direct traffic through it - based on traffic type, source IPs/MAC, etc. I recognise this one would likely be non-trivial! Less important to me is having the image automatically updated with latest libraries. I recognise many patches are to remediate vulnerabilities, but I'd be happy enough to just see an alert about key ones (openssl, etc?) install required updates myself. If I forget to do this for a few months (or wait for your next major image version ;) then either way I've still got a more secure network than 99% out there. Flipping the question, what about your desires? Are you mainly using this as a hobby project to learn more (about OpenWrt, etc) or do you hope to ultimately use it in a particular way? On Fri, 12 Jun 2020 at 22:18, Grommish [via Itus Networks Owners Forum] <[hidden email]> wrote: Thanks Gnomad.
OpenWrt SNAPSHOT, r10391-3d8d528939
|
|
Hi Grommish You've done some great work on the shield, way above my knowledge level and greatly appreciated. I bought the Shield solely for snort facilities and it sits on the edge of my networks. I use the Shield since your work for Router mode Snort Ad blocker (was using pi hole) What I would like is basically what Gonmad said. What everyone in life wants is simplicity to install, use and when to update. 1. Router mode 2. Snort, with self-updating community rules as a baseline 3. Ad Blocker 4. Alert when updated package are available i.e openssl Again great work Grommish, hope you continue working on the project as I think without you it will die. Roadrunnere42 On Sat, 13 Jun 2020 at 02:46, Gnomad [via Itus Networks Owners Forum] <[hidden email]> wrote:
|
|
I can echo lots of whats been said here already. I had a good router at the time (AVM Fritzbox) which I used for VOIP and other things so wanted to retain that as my main device. At the time I was also port forwarding for games etc so wanted to avoid double nat. As my IoT devices grew I did wonder what those little web servers might be up to and although I had most of them on a segregated wifi (via the fritzbox) I wanted more protection, that and my kids were getting into the internet so that always made me nervous, as much as you can help point them in the ways of good, easy to download something malicious that could sit on my network stealthily.
The Shield came along by chance as it was mentioned in a podcast I subscribed to and it seemed to be exactly what I'd been looking for. I'd read about the advantages and dissadvantages of Deep Packet Inspection. Some things which initially attracted me: - that this used a ''special Cavium procressor which was meant to optimise the packet inspection - the 'set it and forget it' (more or less) apsect of this device - the fact that it could sit between my perfectly good router and the rest of my network in bridge mode ao I could retain my current routers functionaility. As it turned out the 'set it and forget it' was never really a thing and I had problems from day 1 which involved lots of conversations with itus techs. It only really became useful and stable once itus folded and this wonderful community took it and made it work! I am forever grateful to all the indivuals who helped with that and the support I recevied, some are still here some have moved on, but the fact that you are taking time now Grommish is really appreciated and as stated, if you were not doing this it's doubtful anyone else would be motivated to. I moved from the Fritzxbox/shield to a Sophos applicance + AP which took me ages to configure and get my head around but eventually I did and liked it for a while but it was high maintenance in the end due to the 50 IP limit of the free version so I went to the market again. I now have a Synology Router with Deep Packet Inspection (add-in program called called Threat prevention) which is a signature based system which is initially quite noisy until you dial in to the right level of notifications. It's very low maintenance now and updates are all taken care of automatically so I really like it. I also use Pi-Hole so between these devices I'm fairly well set so difficult to know if/where the Shield could provide value for me, other than the joy of tinkering which I do enjoy when I get time and I've learned a lot over the years, that's for sure. So, looking forward to seeing what comes of the requirements here, for me I would say Threat provention, Ad blocking and LOW maintenance are key. Bridged if possible. I've been racking my brains to think of what other uses a cool little 3 port, CAvium powered device could be used for, but not really come up with much yet :) Cheers
Running v2 Firmware
|
|
Administrator
|
Thanks for the input all!
My background is in InfoSec and Networking, so the Shield (iGuardian,damnit) caught my attention right away. I used to build Android ROMs, which led me to OpenWrt :) So, the consensus seems to be Ease of use and IDS/IPS. The image I have basically covers that.. But, it's not readily updatable without wiping out everything. Ok, so, does anyone have a preference in which to use? snort is popular.. Suricata is popular.. I was even looking at OSSEC HIDS for a bit.. I'm not sure which would be easier to use. I suspect snort+, but then we get into the issues of dealing with TLS/SSL/encrypted traffic.. In order for it to be effective, it'll need to do that. This means setting the shield up as a reverse-proxie and making sure the Key is installed on every client machine (I think.. more research is needed). It just is going to be one of those things that needs to be decided on the best way to go. I'd really like to be able to solve this update issue regardless..
Running Itus Shield v2 Firmware
|
|
Administrator
|
Also.. check this out.. :D
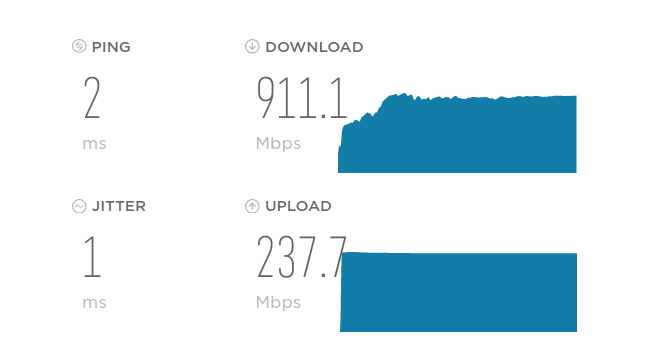 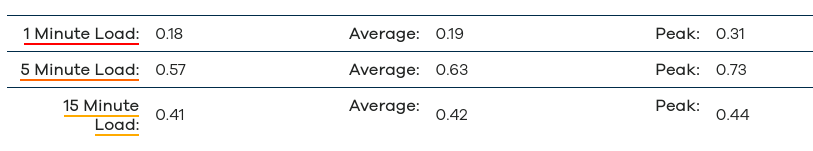 Through the Shield, but snort isn't running.. With snort running (and running a 564m process!) the speeds drop some, but I know with some optimizations, they would probably be better.. 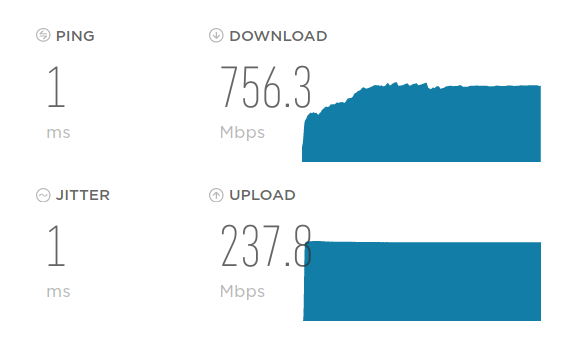 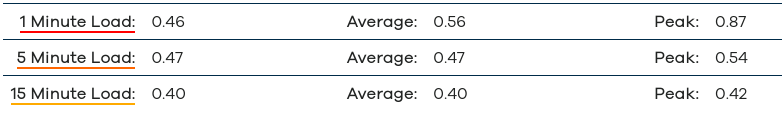
Running Itus Shield v2 Firmware
|
|
Administrator
|
Who wants to guess what this is?
Running Itus Shield v2 Firmware
|
|
Judging by the file name, nothing good?
Running v2 Firmware
|
|
In reply to this post by Grommish
Your cat leaning on the keyboard? On Sun, 14 Jun 2020 at 15:38, Grommish [via Itus Networks Owners Forum] <[hidden email]> wrote: Who wants to guess what this is?
OpenWrt SNAPSHOT, r10391-3d8d528939
|
«
Return to Technical Discussion
|
1 view|%1 views
| Free forum by Nabble | Edit this page |


